Secure Gate: Secure Gateways and Wireless Sensors as Enablers for Sustainability in Production Plants
Gateway for Industrial Cyber-Physical Systems with Hardware-based Trust Anchors
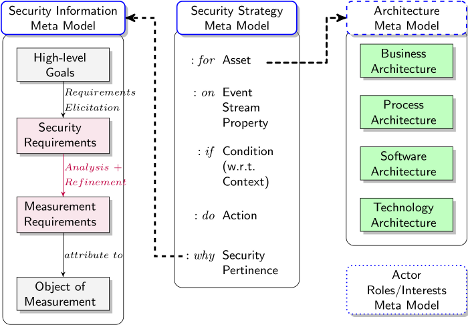 Actionable knowledge for security incident response is information that can be acted upon to prevent, mitigate, or eliminate threats. A security strategy model should span all parts of the security monitoring and decision support process, namely: I. detecting threatening events; II. putting them in context of the current system state and explaining their potential impact with respect to some security- or compliance model; and III. taking appropriate actions. In order to implement a security strategy, systems require an appropriate architecture and security mechanisms for detecting threatening events as well as to take appropriate actions. |
Sensors, ML, TPM-measurements 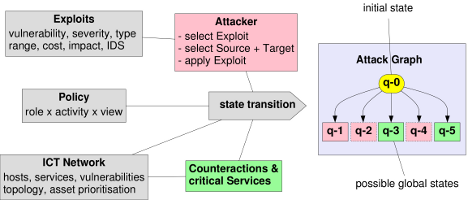 Knowledge represented by operational models allows to analyse the behaviour of cooperating systems with respect to security and dependability properties. Usually only a few characteristic actions of the system are of interest with respect to analysis of security critical behaviour. So it is evident to define 'property preserving' abstractions with respect to the actions of interest. By utilising this model, a goal-oriented security metric reflecting security assessment with respect to security goals of the responsible stakeholder could be derived. This in turn can be used to optimise a system configuration in order to minimise the attack surface. Trusted Gateway; Adapted system behaviour |
| Diethelm Bienhaus, Andreas Ebner, Lukas Jäger, Roland Rieke, and Christoph Krauß, Secure Gate: Secure Gateways and Wireless Sensors as Enablers for Sustainability in Production Plants, Elsevier Journal: Simulation Modelling Practice and Theory, 2021 |
| Abstract: The Internet of Things has reached the industry. Allowing connectivity from the shop floor to the Internet requires appropriate security mechanisms to provide protection against cyber attackers. In this paper, we propose a security architecture for a gateway connecting sensors and automation components from production lines with Internet or cloud based systems. A Trusted Platform Module 2.0 is used for protecting the cryptographic keys used in secure communication protocols and to provide protection against illegitimate firmware manipulation. As proof of concept, we implemented the key protection functionality with a TPM 2.0 for the OPC UA protocol. In a field test, gateways have been installed together with wireless sensors in production plants. Two significant results with respect to the sustainability objectives of secure remote production, namely, reduction of chemical waste and reduction of electrical energy consumption have been demonstrated. |
| Diethelm Bienhaus, Lukas Jäger, Roland Rieke, and Christoph Krauß (2019), Gateway for Industrial Cyber-Physical Systems with Hardware-based Trust Anchors, IDC2019, St. Petersburg, Russia, October 7-9, 2019 (Springer SCI, volume 868) |
| Abstract: Industrial Cyber-Physical Systems require appropriate security mechanisms to provide protection against cyber attackers. In this paper, we propose a security architecture for a gateway connecting production and cloud systems. A Trusted Platform Module 2.0 is used for protecting the cryptographic keys used in secure communication protocols and to provide protection against illegitimate firmware manipulation. As proof of concept, we implemented the key protection functionality with a TPM 2.0 for the OPC UA protocol. |
BibTeX:
@InProceedings{Bienhaus2019,
author = {Diethelm Bienhaus and Lukas J{\"{a}}ger and Roland Rieke and Christoph Krau{\ss}},
editor = {Igor V. Kotenko and Costin Badica and Vasily Desnitsky and Didier El Baz and Mirjana Ivanovic},
title="Gateway for Industrial Cyber-Physical Systems with Hardware-Based Trust Anchors",
booktitle="Intelligent Distributed Computing XIII",
doi = {10.1007/978-3-030-32258-8\_61},
series = {Studies in Computational Intelligence},
volume = {868},
publisher = {Springer},
year = {2020},
address="Cham",
pages="521--528",
isbn="978-3-030-32258-8"
}
|
| Andre Rein, Roland Rieke, Michael Jäger, Nicolai Kuntze, and Luigi Coppolino (2015), Trust Establishment in Cooperating Cyber-Physical Systems, Security of Industrial Control Systems and Cyber Physical Systems: First Workshop, CyberICS 2015 and First Workshop, WOS-CPS 2015 Vienna, Austria, September 21--22, 2015 Revised Selected Papers (Springer LNCS 9588) [Abstract] [Bibtex] [Paper] [Author's pre-proceedings version] |
| Abstract: Cooperating systems are systems of systems that collaborate for a common purpose. In this work, we consider networked cooperating systems that base important decisions on data gathered from external sensors and use external actuators to enforce safety critical actions. Typical examples of cooperating cyber-physical systems are critical infrastructure process control systems. Such systems must not only be secure, they must be demonstrably so. Using the example of a hydroelectric power plant control system, this paper analyzes security threats for networked cooperating systems, where sensors providing decision critical data are placed in non-protected areas and thus are exposed to various kinds of attacks. We propose a concept for trust establishment in cyber-physical cooperating systems. Using trusted event reporting for critical event sources, the authenticity of the security related events can be verified. Based on measurements obtained with a prototypical realisation, we evaluate and analyze the amount of overhead data transmission between event source and data verification system needed for trust establishment. We propose an efficient synchronisation scheme for system integrity data, reducing network traffic as well as verification effort. |
BibTeX:
@Inbook{Rein2016,
author="Rein, Andre
and Rieke, Roland
and J{\"a}ger, Michael
and Kuntze, Nicolai
and Coppolino, Luigi",
editor="B{\'e}cue, Adrien
and Cuppens-Boulahia, Nora
and Cuppens, Fr{\'e}d{\'e}ric
and Katsikas, Sokratis
and Lambrinoudakis, Costas",
title="Trust Establishment in Cooperating Cyber-Physical Systems",
bookTitle="Security of Industrial Control Systems and Cyber Physical Systems: First Workshop, CyberICS 2015 and First Workshop, WOS-CPS 2015 Vienna, Austria, September 21--22, 2015 Revised Selected Papers",
year="2016",
publisher="Springer International Publishing",
address="Cham",
pages="31--47",
isbn="978-3-319-40385-4",
doi="10.1007/978-3-319-40385-4_3",
series={Lecture Notes in Computer Science},
volume={9588},
url="http://dx.doi.org/10.1007/978-3-319-40385-4_3"
}
|
| Roland Rieke, Maria Zhdanova, and Jürgen Repp (2015), Security and Business Situational Awareness, Cyber Security and Privacy, 4th Cyber Security and Privacy Innovation Forum, CSP Innovation Forum 2015 [Abstract] [Bibtex] [Paper] [Author's version] |
| Abstract: "Security needs to be aligned with business". Business situational awareness is the ability to continually monitor ongoing actions and events related to business operations and estimate the immediate and close-future impact of the new information. This ability is crucial for business continuity and should encompass all associated aspects. Considering the growing dependability of businesses on IT on the one hand, and ever increasing threats on the other, IT security aspects should get adequate attention in the awareness system. We present an approach to raise business situational awareness using an advanced method of predictive security analysis at runtime. It continually observes a system's event stream to find deviations from specified behavior and violations of security compliance rules. Operational models of the key processes are utilized to predict critical security states, evaluate possible countermeasures, and trigger corrective actions. A security information model maintains the security strategy and explains possible deviations from the originating goal. The approach is demonstrated on an industrial scenario from a European research project. |
BibTeX:
@incollection{RZR-CSP2015,
author={Rieke, Roland and Zhdanova, Maria and Repp, J\"urgen},
title={Security and Business Situational Awareness},
year={2015},
isbn={978-3-319-25359-6},
booktitle={Cyber Security and Privacy},
volume={530},
series={Communications in Computer and Information Science},
editor={Cleary, Frances and Felici, Massimo},
doi={10.1007/978-3-319-25360-2_9},
url={http://dx.doi.org/10.1007/978-3-319-25360-2_9},
publisher={Springer International Publishing},
keywords={Predictive security analysis; Process behavior analysis; Security modeling and simulation; Security monitoring; Security strategy; Security information and event management; Governance and compliance},
pages={103-115},
language={English}
}
|
| Julian Schütte, Roland Rieke, and Timo Winkelvos (2012), Model-based Security Event Management, MMM-ACNS 2012, (Springer LNCS 7531) |
| Abstract: With the growing size and complexity of current ICT infrastructures, it becomes increasingly challenging to gain an overview of potential security breaches. Security Information and Event Management systems which aim at collecting, aggregating and processing security-relevant information are therefore on the rise. However, the event model of current systems mostly describes network events and their correlation, but is not linked to a comprehensive security model, including system state, security and compliance requirements, countermeasures, and affected assets. In this paper we introduce a comprehensive semantic model for security event management. Besides the description of security incidents, the model further allows to add conditions over the system state, define countermeasures, and link to external security models. |
BibTeX:
@incollection{mmm-acnsa:2012,
author={Sch\"utte, Julian and Rieke, Roland and Winkelvos, Timo},
title={Model-Based Security Event Management},
year={2012},
isbn={978-3-642-33703-1},
booktitle={Computer Network Security},
volume={7531},
series={Lecture Notes in Computer Science},
editor={Kotenko, Igor and Skormin, Victor},
doi={10.1007/978-3-642-33704-8_16},
url={http://dx.doi.org/10.1007/978-3-642-33704-8_16},
publisher={Springer Berlin Heidelberg},
keywords={security strategy meta model; security information and event management; complex event processing},
pages={181-190}
}
|
| Roland Rieke, Julian Schütte, and Andrew Hutchison (2012), Architecting a Security Strategy Measurement and Management System, MDSec 2012, Proceedings of the Workshop on Model-Driven Security, ACM 2012 [Abstract] [BibTeX] [Paper ACM DL] [Conference Version (free access)] [Author's version] |
| Abstract: The use of formal models to guide security design is appealing. This paper presents a model driven approach whereby security systems in operation can be assessed and measured against various requirements that are defined when the system is created. By aligning with organisational policy, and business requirements of a specific system, design and operation can proceed in a way that allows measurement of how successfully security objectives are being achieved. This paper describes a model driven approach which overcomes the contextual restrictions of existing solutions. In particular, where models have been used previously these have tended to be predefined and closed models, whereas the approach described here is an extensible model that comprises all parts of the security monitoring and decision support process. By means of interlinked semantic concepts, the proposed security strategy meta model provides a way to model security directives at an abstract level, which can be automatically compiled into specific rules for an underlying framework of monitoring, decision support, and enforcement engines. |
BibTeX:
@inproceedings{MDSec:2012,
author = {Rieke, Roland and Sch\"{u}tte, Julian and Hutchison, Andrew},
title = {Architecting a security strategy measurement and management system},
booktitle = {Proceedings of the Workshop on Model-Driven Security},
series = {MDsec '12},
year = {2012},
isbn = {978-1-4503-1806-8},
location = {Innsbruck, Austria},
pages = {2:1--2:6},
articleno = {2},
numpages = {6},
url = {http://doi.acm.org/10.1145/2422498.2422500},
doi = {10.1145/2422498.2422500},
acmid = {2422500},
publisher = {ACM},
address = {New York, NY, USA},
keywords = {decision support, governance and compliance, information security measurement model, security information and event management, security monitoring, security strategy},
}
|
| Luigi Coppolino, Michael Jäger, Nicolai Kuntze, and Roland Rieke (2012), A Trusted Information Agent for Security Information and Event Management, The Seventh International Conference on Systems (ICONS 2012) [Abstract] [BibTeX] [Paper (free access)] [Author's version] |
| Abstract: This paper addresses security information management in untrusted environments. A security information and event management system collects and examines security related events and provides a unifying view of the monitored system's security status. The sensors, which provide the event data, are typically placed in a non-protected environment at the boarder of the managed system. They are exposed to various kinds of attacks. Compromised sensors may lead to misjudgement on the system's state with possibly serious consequences. The particular security requirements arising from these problems are discussed for large scale critical infrastructures. The main contribution of this paper is a concept that provides trusted event reporting. Critical event sources are holistically protected such that authenticity of the security related events is guaranteed. This enables better assessment of the managed system's reliability and trustworthiness. As a proof of this concept, the paper presents an exemplary realisation of a trustworthy event source. |
BibTeX:
@incollection{cjkr:2012,
author = {Luigi Coppolino and Michael J\"ager and Nicolai Kuntze and Roland Rieke},
title = {{A Trusted Information Agent for Security Information and Event Management}},
booktitle = {ICONS 2012, The Seventh International Conference on Systems, February 29 - March 5, 2012 - Saint Gilles, Reunion Island},
pages = {6-12},
url = {http://www.thinkmind.org/download.php?articleid=icons_2012_1_20_20062},
publisher={IARIA},
isbn={978-1-61208-184-7},
year = {2012}
}
|
| Andreas Fuchs and Roland Rieke (2010), Identification of Security Requirements in Systems of Systems by Functional Security Analysis, In Architecting Dependable Systems VII, (Springer LNCS 6420) |
| Abstract: Cooperating systems typically base decisions on information from their own components as well as on input from other systems. Safety critical decisions based on cooperative reasoning however raise severe concerns to security issues. Here, we address the security requirements elicitation step in the security engineering process for such systems of systems. The method comprises the tracing down of functional dependencies over system component boundaries right onto the origin of information as a functional flow graph. Based on this graph, we systematically deduce comprehensive sets of formally defined authenticity requirements for the given security and dependability objectives. The proposed method thereby avoids premature assumptions on the security architecture's structure as well as the means by which it is realised. Furthermore, a tool-assisted approach that follows the presented methodology is described. |
BibTeX:
@incollection{fuchs:rieke:2010,
author = {Andreas Fuchs and Roland Rieke},
title = {{Identification of Security Requirements in Systems of Systems by Functional Security Analysis}},
booktitle = {Architecting Dependable Systems VII},
editor = {Antonio Casimiro and Rogério de Lemos and Cristina Gacek},
publisher = {Springer},
series = {Lecture Notes in Computer Science},
volume = {6420},
year = {2010},
pages = {74--96},
doi={10.1007/978-3-642-17245-8_4},
url={http://dx.doi.org/10.1007/978-3-642-17245-8_4},
isbn = {978-3-642-17244-1}
}
|
| Andreas Fuchs and Roland Rieke (2009), Identification of authenticity requirements in systems of systems by functional security analysis, In Workshop on Architecting Dependable Systems (WADS 2009), in Proceedings of the 2009 IEEE/IFIP Conference on Dependable Systems and Networks, Supplemental Volume. |
| Abstract: Cooperating systems typically base decisions on information from their own components as well as on input from other systems. Safety critical decisions based on cooperative reasoning, such as automatic emergency braking of a vehicle, raise severe concerns to security issues. In this paper we address the security engineering process for such systems of systems. The presented authenticity requirements elicitation method is based on functional dependency analysis. It comprises the tracing down of functional dependencies over system boundaries right onto the origin of information. A dependency graph with a safety critical function as root and the origins of decision relevant information as leaves is used to deduce a set of authenticity requirements. This set is comprehensive and defines the maximal set of authenticity requirements from the given functional dependencies. Furthermore, the proposed method avoids premature assumptions on the architectural structure and mechanisms to implement security measures. |
BibTeX:
@inproceedings{fuchs:rieke:2009,
author = {Andreas Fuchs and Roland Rieke},
title = {Identification of authenticity requirements in systems of systems by functional security analysis},
booktitle = {Workshop on Architecting Dependable Systems (WADS 2009), in Proceedings of the 2009 IEEE/IFIP Conference on Dependable Systems and Networks, Supplemental Volume},
year = {2009},
pages={E29-E34},
}
|
| Roland Rieke (2008), Abstraction-based analysis of known and unknown vulnerabilities of critical information infrastructures, International Journal of System of Systems Engineering (IJSSE). Vol. 1, pp. 59-77. InderScience. |
| Abstract: The systematic protection of critical information infrastructures requires an analytical process to identify the critical components and their interplay, to determine the threats and vulnerabilities, to assess the risks and to prioritise countermeasures where risk is unacceptable. The abstraction-based approach presented here builds on a model-based construction of an attack graph with constraints given by the network security policy. A unique feature of the presented approach is, that abstract representations of these graphs can be computed that allow comparison of focussed views on the behaviour of the system. In order to analyse resilience of critical information infrastructures against exploits of unknown vulnerabilities, generic vulnerabilities for each installed product and affected service are added to the model. The reachability analysis now considers every possible choice of product, and so all alternatives are evaluated in the attack graph. The impact of changes to security policies or network structure can be visualised by differences in the attack graphs. Results of this analysis support the process of dependable configuration of critical information infrastructures. |
BibTeX:
@article{Rieke08,
author = {Roland Rieke},
title = {Abstraction-based analysis of known and unknown vulnerabilities of critical information infrastructures},
journal = {International Journal of System of Systems Engineering (IJSSE)},
publisher = {Inderscience},
year = {2008},
volume = {1},
number={1/2},
pages = {59-77},
issn = {1748-0671},
doi={10.1504/IJSSE.2008.018131},
url ={http://dx.doi.org/10.1504/IJSSE.2008.018131}
}
|
| Peter Ochsenschläger, Roland Rieke, and Zaharina Velikova (2008), Die elektronische Krankenakte - Eine Sicherheitsstrategie, In DACH Security 2008 - Bestandsaufnahme, Konzepte, Anwendungen, Perspektiven. |
| Abstract: Diese Arbeit stellt ein Organisationsstruktur-basiertes Berechtigungskonzept am Beispiel der elektronischen Krankenakte vor. Ein ausführbares Modell der Sicherheitsstrategie erlaubt die vollständige Analyse des Systemverhaltens. Durch eigenschaftserhaltende Abstraktionen wird daraus eine kompakte Visualisierung von spezifischen Aspekten dieses Verhaltens möglich. Wegen der Kompaktheit der Darstellung lassen sich daraus die gewünschten Systemeigenschaften unmittelbar ablesen. Da die gewählten Abstraktionen eigenschaftserhaltend sind, folgen daraus nicht nur die erforderlichen Sicherheitseigenschaften sondern auch die Funktionssicherheit eines solchen Berechtigungskonzeptes trotz der gebotenen Datensparsamkeit. |
BibTeX:
@inproceedings{ORV08,
author = {P. Ochsenschläger and R. Rieke and Z. Velikova},
title = {Die elektronische Krankenakte - Eine Sicherheitsstrategie},
booktitle = {DACH Security 2008 - Bestandsaufnahme, Konzepte, Anwendungen, Perspektiven.},
year = {2008},
month = {June},
pages = {90-100},
isbn={978-3-00-024632-6}
}
|
| Apel, C., Jürgen Repp, Rieke, R., and Steingruber, J. (2007), Modellbasiertes Testen der deutschen Gesundheitskarten, In DACH Security 2007 - Bestandsaufnahme, Konzepte, Anwendungen, Perspektiven. |
| Abstract: Dieser Beitrag beschreibt die Anwendung eines modellbasierten Verfahrens zur Testfolgengenerierung auf die deutschen elektronischen Gesundheitskarten, Heilberufsausweise und Sicherheitsmodulkarten, um deren Datensicherheit, Interoperabilität und Robustheit zu testen. Zur Modellierung der Chipkartenanwendungen werden asynchrone Produktautomaten (APA) verwendet. Daraus werden abstrakte Kommandofolgen für die Chipkarten berechnet, die dann in einem weiteren Schritt in konkrete ausführbare Kommandos übersetzt werden. Das verwendete Verfahren hat den Vorteil, dass damit komplexe Chipkartenanwendungen in kompakter und übersichtlicher Weise modelliert und automatisiert Testfolgen mit hoher Testabdeckung erzeugt werden können. |
BibTeX:
@inproceedings{ARRS07,
author = {C. Apel and J. Repp and R. Rieke and J. Steingruber},
title = {Modellbasiertes Testen der deutschen Gesundheitskarten},
booktitle = {DACH Security 2007 - Bestandsaufnahme, Konzepte, Anwendungen, Perspektiven.},
year = {2007},
month = {June},
pages = {338-346},
isbn={978-3-00-021600-8}
}
|
| Peters, J., Rieke, R., Rochaeli, T., Steinemann, B., and Wolf, R. (2007), A Holistic Approach to Security Policies - Policy Distribution with XACML over COPS, In Proc. of the Second International Workshop on Views On Designing Complex Architectures (VODCA 2006). February 2007. Volume 168, Elsevier. |
| Abstract: The potentials of modern information technology can only be exploited, if the underlying infrastructure and the applied applications sufficiently take into account all aspects of IT security. This paper presents the platform architecture of the SicAri project, which aims to build a security platform for ubiquitous Internet usage, and gives an overview of the implicitly and explicitly used security mechanisms to enable access control for service oriented applications in distributed environments. The paper will introduce the security policy integration concept with a special focus on distribution of security policies within the service infrastructure for transparent policy enforcement. We describe in details our extensions of the COPS protocol to transport XACML payload for security policy distribution and policy decision requests/responses. |
BibTeX:
@inproceedings{Peters06,
author = {Jan Peters and Roland Rieke and Taufiq Rochaeli and Bj\"orn Steinemann and Ruben Wolf},
title = {{A Holistic Approach to Security Policies -- Policy Distribution with XACML over COPS}},
booktitle = {Proc. of the Second International Workshop on Views On Designing Complex Architectures (VODCA 2006)},
journal = {Electronic Notes in Theoretical Computer Science},
publisher = {Elsevier},
year = {2007},
month= {February},
volume = {168},
pages = {143-157},
issn = {1571-0661},
doi = {10.1016/j.entcs.2006.08.025},
url = {http://www.sciencedirect.com/science/article/pii/S1571066107000333},
}
|
| Roland Rieke (2006), Modelling and Analysing Network Security Policies in a Given Vulnerability Setting, In Critical Information Infrastructures Security, First International Workshop (CRITIS 2006), (Springer LNCS 4347) |
| Abstract: The systematic protection of critical information infrastructures requires an analytical process to identify the critical components and their interplay, to determine the threats and vulnerabilities, to assess the risks and to prioritise countermeasures where risk is unacceptable. This paper presents an integrated framework for model-based symbolic interpretation, simulation and analysis with a comprehensive approach focussing on the validation of network security policies. A graph of all possible attack paths is automatically computed from the model of an ICT network, of vulnerabilities, exploits and an attacker strategy. Constraints on this graph are given by a model of the network security policy. The impact of changes to security policies can be computed and visualised by finding differences in the attack graphs. A unique feature of the presented approach is, that abstract representations of these graphs can be computed that allow comparison of focussed views on the behaviour of the system. This guides optimal adaptation of the security policy to the given vulnerability setting. |
BibTeX:
@incollection{Rieke06,
author = {Roland Rieke},
title = {{Modelling and Analysing Network Security Policies in a Given Vulnerability Setting}},
booktitle = {Critical Information Infrastructures Security, First International Workshop, CRITIS 2006, Samos Island, Greece. Revised Papers},
editor={Javier Lopez},
year = {2006},
series = {Lecture Notes in Computer Science},
volume = {4347},
pages = {67-78},
isbn={978-3-540-69083-2},
doi={10.1007/11962977_6},
url={http://dx.doi.org/10.1007/11962977_6},
publisher={Springer Berlin Heidelberg},
keywords={threats analysis; attack simulation; critical infrastructure protection; network security policies; risk assessment; security modelling and simulation}
}
|
| Roland Rieke (2004), Tool based formal Modelling, Analysis and Visualisation of Enterprise Network Vulnerabilities utilising Attack Graph Exploration, In U.E. Gattiker (Ed.), Eicar 2004 Conference CD-rom: Best Paper Proceedings. |
| Abstract: A core concern of critical infrastructure protection is a careful analysis of what parts of the information infrastructure really need protection and what are the concrete threads as well as an evaluation of appropriate protection measures. In this paper a methodology and a tool for the development and analysis of operational formal models is presented that addresses these issues in the context of network vulnerability analysis. A graph of all possible attack paths is automatically computed from the model of a government or enterprise network, of vulnerabilities, exploits and an attacker strategy. Based on this graph, security properties are specified and verified, abstractions of the graph are computed to visualise and analyse compacted information focussed on interesting aspects of the behaviour and cost-benefit analysis is performed. Survivability comes into play, when systems' countermeasures and the behaviour of vital services it provides are also modelled and effects are analysed. |
BibTeX:
@inproceedings{EICAR2004,
author = {Roland Rieke},
title = {Tool based formal Modelling, Analysis and Visualisation of Enterprise Network Vulnerabilities utilising Attack Graph Exploration},
booktitle = {In U.E. Gattiker (Ed.), Eicar 2004 Conference CD-rom: Best Paper Proceedings},
year = {2004},
month = {May},
location ={Copenhagen},
url = {http://publica.fraunhofer.de/dokumente/N-47447.html}
}
|
| Roland Rieke (2003), Development of formal models for secure e-services, In Eicar Conference 2003. |
BibTeX:
@inproceedings{EICAR2003,
author = {Roland Rieke},
title = {Development of formal models for secure e-services},
booktitle = {Eicar Conference 2003},
year = {2003},
month ={May},
}
|
| Roland Rieke (2002), Implementing the APA model for the symmetric Needham-Schroeder protocol in state transition pattern notation in the SH Verification Tool, Technical Report |
BibTeX:
@techreport{other-NS-TR:2002,
author = {Roland Rieke},
title = {{Implementing the APA model for the symmetric Needham-Schroeder protocol in state transition pattern notation in the SH Verification Tool}},
year = {2002},
institution={Fraunhofer Institute for Secure Telecooperation SIT},
url = {http://rieke.link/NS-TR2002.pdf}
}
|
| Peter Ochsenschläger, Jürgen Repp, and Roland Rieke (2002), Simple Homomorphism Verification Tool - Tutorial Manual |
BibTeX:
@manual{shvttutorial,
author = {Peter Ochsenschl\"ager and J\"urgen Repp and Roland Rieke},
title = {Simple Homomorphism Verification Tool -- Tutorial},
year = {2002},
url = {http://publica.fraunhofer.de/dokumente/N-47733.html}
}
|
| Peter Ochsenschläger, Jürgen Repp, and Roland Rieke (2000), The SH-Verification Tool, In Proc. 13th International Florida Artificial Intelligence Research Society Conference (FLAIRS-2000), AAAI Press. |
BibTeX:
@inproceedings{Ochsenschlaeger:Repp:Rieke:2000b,
author = {Peter Ochsenschl\"ager and J\"urgen Repp and Roland Rieke},
title = {The SH-Verification Tool},
booktitle = {Proc. 13th International Florida Artificial Intelligence Research Society Conference (FLAIRS-2000)},
publisher = {AAAI Press},
location={Orlando, FL, USA},
year = {2000},
month= {May},
pages = {18-22},
note = {Copyright: 2000, American Association for Artificial Intelligence (www.aaai.org). All rights reserved.},
url = {http://www.aaai.org/Papers/FLAIRS/2000/FLAIRS00-004.pdf}
}
|
| Peter Ochsenschläger, Jürgen Repp, Roland Rieke, and Ulrich Nitsche (1998), The SH-Verification Tool - Abstraction-Based Verification of Co-operating Systems, Formal Aspects of Computing, The International Journal of Formal Methods, Vol. 10. |
BibTeX:
@article{ORRN:98,
author = {Peter Ochsenschläger and J\"urgen Repp and Roland Rieke and Ulrich Nitsche},
title = {The SH-Verification Tool -- Abstraction-Based Verification of Co-operating Systems},
journal = {Formal Aspects of Computing, The International Journal of Formal Methods},
year = {1998},
volume = {10},
issue = {4},
pages = {381-404},
publisher={Springer-Verlag London Limited},
doi={10.1007/s001650050023},
issn={0934-5043},
url = {http://link.springer.com/article/10.1007\%2Fs001650050023}
}
|