Florian Fenzl, Jonathan Stancke, Felix Gail, Christian Plappert, Roland Rieke, Theo Dimitrakos, Hussein Joumaa
SecPol: Enabling Security Policy Control in Vehicle Networks using Intrusion Detection and Hardware Trust
,
accepted at 1st Cyber Security in Cars Workshop (CSCS) at ACM CCS 2024
[Abstract]
[Bibtex]
[Paper (open access)]
|
| Abstract:
As vehicle networks become more complex to enable more advanced features like autonomous driving, their cyberattack surface
increases. Containing such cyberattacks always requires more sophisticated and adaptive security approaches. The secure implementation of usage control systems for use in vehicle networks is
particularly important, as increasing communication with external entities offers attackers new opportunities to penetrate such
networks. Modern off-the-shelf access management systems have
difficulty dynamically adapting to new situations or responding
to potential attacks. To improve the security and adaptability of
policy-driven usage control systems, we propose the integration of
additional in-vehicle security measurement and verification mechanisms based on intrusion detection and hardware trust anchors. This
allows to incorporate boot and runtime security incidents into appropriate policy decisions. We discuss the possible uses and effects
of this approach using common intrusion scenarios as examples,
and evaluate the approach with two exemplary implementations
based on an open-source and a proprietary usage control system.
Finally, we propose an architecture to integrate the recommended
security measures into security incident processing controlled by a
security operations center. The use cases given are from the automotive sector, but variations of the protocols and communication
mechanisms are also used in airplanes and trains, and the approach
can therefore be extended to multimodal applications.
|
BibTeX:
@inproceedings{Fenzl2024,
author = {Fenzl, Florian and Stancke, Jonathan and Plappert, Christian and Rieke, Roland and Gail, Felix and Dimitrakos, Theo and Joumaa, Hussein},
title = {SecPol: Enabling Security Policy Control in Vehicle Networks using Intrusion Detection and Hardware Trust},
year = {2024},
isbn = {9798400712326},
publisher = {Association for Computing Machinery},
address = {New York, NY, USA},
url = {https://doi.org/10.1145/3689936.3694697},
doi = {10.1145/3689936.3694697},
abstract = {As vehicle networks become more complex to enable more advanced features like autonomous driving, their cyberattack surface increases. Containing such cyberattacks always requires more sophisticated and adaptive security approaches. The secure implementation of usage control systems for use in vehicle networks is particularly important, as increasing communication with external entities offers attackers new opportunities to penetrate such networks. Modern off-the-shelf access management systems have difficulty dynamically adapting to new situations or responding to potential attacks. To improve the security and adaptability of policy-driven usage control systems, we propose the integration of additional in-vehicle security measurement and verification mechanisms based on intrusion detection and hardware trust anchors. This allows to incorporate boot and runtime security incidents into appropriate policy decisions. We discuss the possible uses and effects of this approach using common intrusion scenarios as examples, and evaluate the approach with two exemplary implementations based on an open-source and a proprietary usage control system. Finally, we propose an architecture to integrate the recommended security measures into security incident processing controlled by a security operations center. The use cases given are from the automotive sector, but variations of the protocols and communication mechanisms are also used in airplanes and trains, and the approach can therefore be extended to multimodal applications and other resource-constraint IOT networks.},
booktitle = {Proceedings of the 2024 Cyber Security in CarS Workshop},
pages = {25-38},
numpages = {14},
keywords = {authorization, automotive ethernet, automotive security, autosar, can, controller area network, intrusion detection, intrusion prevention, policy management, trusted computing, usage control},
location = {Salt Lake City, UT, USA},
series = {CSCS '24}
}
|
Davide Micale, Ilaria Matteucci, Florian Fenzl, Roland Rieke, Giuseppe Patanè
A context-aware on-board intrusion detection system for smart vehicles,
International Journal of Information Security 2024
[Abstract]
[Bibtex]
[Paper (open access)]
|
| Abstract:
Modern vehicles are becoming more appealing to potential intruders due to two primary reasons. Firstly, they are now equipped with various connectivity features like WiFi, Bluetooth, and cellular connections, e.g., LTE and 5G, which expose them to external networks. Secondly, the growing complexity of on-board software increases the potential attack surface. In this article, we introduce CAHOOTv2, a context-sensitive intrusion detection system (IDS), aiming at enhancing the vehicle's security and protect against potential intrusions. CAHOOTv2 leverages the vehicle's sensors data, such as the amount of steering, the acceleration and brake inputs, to analyze driver habits and collect environmental information. To demonstrate the validity of the algorithm, we collected driving data from both an artificial intelligence (AI) and 39 humans. We include the AI driver to demonstrate that CAHOOTv2 is able to detect intrusions when the driver is both a human or an AI. The dataset is obtained using a modified version of the MetaDrive simulator, taking into account the presence of an intruder capable of performing the following types of intrusions: denial of service, replay, spoofing, additive and selective attacks. The sensors present in the vehicle are a numerical representation of the environment. The amount of steering, the acceleration and brake inputs given by the driver are based on the environmental situation. The intruder's input often contradicts the driver's wishes. CAHOOTv2 uses vehicle sensors to detect this contradiction. We perform several experiments that show the benefits of hyperparameter optimization. Indeed, we use a hyperparameter tuning paradigm to increase detection accuracy combining randomized and exhaustive search of hyperparameters. As a concluding remark, the results of CAHOOTv2 show great promise in detecting intrusions effectively.
|
BibTeX:
@article{Micale2024,
author={Davide Micale, Ilaria Matteucci, Florian Fenzl, Roland Rieke, Giuseppe Patanè},
journal={International Journal of Information Security},
title={A context-aware on-board intrusion detection system for smart vehicles},
doi=(https://doi.org/10.1007/s10207-024-00821-3},
publisher={Springer},
year={2024},
month={March}}
|
Marco De Vincenzi, Gianpiero Costantino, Ilaria Matteucci, Florian Fenzl, Christian Plappert, Roland Rieke, Daniel Zelle
A Systematic Review on Security Attacks and Countermeasures in Automotive Ethernet,
ACM Computing Surveys 2024
[Abstract]
[Bibtex]
[Paper (open access)]
|
| Abstract:
In the last years, the automotive industry has experienced a technological revolution driven by the increasing
demand of connectivity and data to develop driver-assistance systems, autonomous vehicles, and improve the
mobility experience. To provide higher bandwidth in in-vehicle communication networks (IVNs), carmakers
are choosing Ethernet technology, which becomes Automotive Ethernet when applied in IVNs. However, with
the rise of vehicle connectivity, the cybersecurity of vehicle systems has become a primary concern for the
automotive industry. To address this issue, we conducted a systematic review, deeply analyzing the impact
of Automotive Ethernet on security, safety, and comparing it with the current in-vehicle communication
solutions like CAN protocol. We retrieved the key security attacks and mitigations proposed in the current
literature to highlight their significance, including a mapping between the regulation UNECE WP.29 R155 and
the retrieved answers. We found that the industry has only implemented some automotive-dedicated Ethernet
solutions to date. In the near future, the vehicle and road ecosystems may require more exclusive automotive
solutions to meet specific constraints such as low latency. Our results can provide a comprehensive baseline,
both for industry and academia, for the current and future development of Automotive Ethernet.
|
BibTeX:
@article{deVincenzi2023,
author = {De Vincenzi, Marco and Costantino, Gianpiero and Matteucci, Ilaria and Fenzl, Florian and Plappert, Christian and Rieke, Roland and Zelle, Daniel},
title = {A Systematic Review on Security Attacks and Countermeasures in Automotive Ethernet},
year = {2023},
publisher = {Association for Computing Machinery},
address = {New York, NY, USA},
issn = {0360-0300},
url = {https://doi.org/10.1145/3637059},
doi = {10.1145/3637059},
abstract = {In the last years, the automotive industry has experienced a technological revolution driven by the increasing demand of connectivity and data to develop driver-assistance systems, autonomous vehicles, and improve the mobility experience. To provide higher bandwidth in in-vehicle communication networks (IVNs), carmakers are choosing Ethernet technology, which becomes Automotive Ethernet when applied in IVNs. However, with the rise of vehicle connectivity, the cybersecurity of vehicle systems has become a primary concern for the automotive industry. To address this issue, we conducted a systematic review, deeply analyzing the impact of Automotive Ethernet on security, safety, and comparing it with the current in-vehicle communication solutions like CAN protocol. We retrieved the key security attacks and mitigations proposed in the current literature to highlight their significance, including a mapping between the regulation UNECE WP.29 R155 and the retrieved answers. We found that the industry has only implemented some automotive-dedicated Ethernet solutions to date. In the near future, the vehicle and road ecosystems may require more exclusive automotive solutions to meet specific constraints such as low latency. Our results can provide a comprehensive baseline, both for industry and academia, for the current and future development of Automotive Ethernet.},
note = {Just Accepted},
journal = {ACM Comput. Surv.},
month = {dec},
keywords = {UNECE R155, automotive, OSI model, Ethernet, safety, security}
}
|
Felix Gail, Roland Rieke, Florian Fenzl, Christoph Krauß
Evaluation of Decision Tree-Based Rule Derivation for Intrusion Detection in Automotive Ethernet ,
The International Symposium on Intelligent and Trustworthy Computing, Communications, and Networking (ITCCN-2023) in conjunction with the 22nd IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom-2023)
[Abstract]
[Bibtex]
[Paper ]
|
| Abstract:
The digitization and networking of safety-critical systems
also enables attacks that can have devastating consequences.
Thus, appropriate security measures are required.
In this work, we investigate a novel approach for security monitoring
adapted to the requirements and properties of safety-critical
systems. In particular, we evaluate and adapt a decision tree-based
detection method that is not only explainable in the sense
that the internal processes of the software can be explained to the
decision maker, but we use the decision tree and the generated
rules to understand exactly which attributes of a message are
used for identification of the attack were used. This supports
experts in the decision-making process and can also be used
for automated countermeasure generation. We demonstrate the
detection method on an Automotive Ethernet protocol that is
being introduced in modern vehicles to replace or complement
currently used bus communication.
|
BibTeX:
@INPROCEEDINGS{Gail2023b,
author={Gail, Felix and Rieke, Roland and Fenzl, Florian and Krauß, Christoph},
booktitle={2023 IEEE 22nd International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom)},
title={Evaluation of Decision Tree-Based Rule Derivation for Intrusion Detection in Automotive Ethernet},
year={2023},
volume={},
number={},
pages={1392-1399},
keywords={Privacy;Protocols;Ethernet;Particle measurements;Generators;Security;Decision trees;Security of Connected Vehicles;Intrusion Detection;Automated Rule Generation;Machine Learning;Anomaly Detection;Decision Trees;Automotive Ethernet},
doi={10.1109/TrustCom60117.2023.00190},
ISSN={2324-9013},
month={Nov},}
|
Felix Gail, Roland Rieke, Florian Fenzl
RulEth: Genetic Programming-Driven Derivation of Security Rules for Automotive Ethernet,
European Conference on Machine Learning and Principles and Practice of Knowledge Discovery in Databases
(ECML PKDD 2023 best paper award for the Applied Data Science track)
[Abstract]
[Bibtex]
[Paper ]
|
| Abstract:
Handcrafted rule-based intrusion detection systems tend to overlook sophisticated intrusions due to unexpected cyberattacker behaviors or human error in analyzing complex control flows. Current machine learning systems, mostly based on artificial neural networks, have the inherent problem that models cannot be verified since the decisions depend on probabilities. To bridge the gap between handcrafted rule systems and probability-based systems, our approach uses genetic programming to generate rules that are verifiable, in the sense that one can confirm that the extracted pattern matches a known attack. The RulEth rules language is designed to be predictive of a packet window, which allows the system to detect anomalies in message flow. Alerts are enriched to include the root cause about the characterization as an anomalous event, which in turn supports decisions to trigger countermeasures. Although the attacks examined in this work are far more complex than those considered in most other works in the automotive domain, our results show that most of the attacks examined can be well identified.
By being able to evaluate each rule generated separately, the rules that are not working effectively can be sorted out, which improves the robustness of the system. Furthermore, using design flaws found in a public dataset, we demonstrate the importance of verifiable models for reliable systems.
|
BibTeX:
@INPROCEEDINGS{Gail2023,
author = {Felix Gail and Roland Rieke and Florian Fenzl},
editor = {Gianmarco De Francisci Morales and Claudia Perlich and Natali Ruchansky and
Nicolas Kourtellis and Elena Baralis and Francesco Bonchi},
title = {RulEth: Genetic Programming-Driven Derivation of Security Rules for Automotive Ethernet},
booktitle = {Machine Learning and Knowledge Discovery in Databases: Applied Data
Science and Demo Track - European Conference, {ECML} {PKDD} 2023,
Turin, Italy, September 18-22, 2023, Proceedings, Part {VII}},
series = {Lecture Notes in Computer Science},
volume = {14175},
pages = {192--209},
publisher = {Springer},
year = {2023},
url = {https://doi.org/10.1007/978-3-031-43430-3\_12},
doi = {10.1007/978-3-031-43430-3\_12},
month = {September}}
|
Florian Fenzl, Christian Plappert, Roland Rieke, Daniel Zelle, Gianpiero Costantino, Marco De Vincenzi and Ilaria Matteucci
Collaborative Security Patterns for Automotive Electrical/Electronic Architectures,
Collaborative Approaches for Cyber Security in Cyber-Physical Systems, Springer 2023
[Abstract]
[Bibtex]
[Paper ]
|
| Abstract:
In this chapter, we describe several security design patterns that collaboratively consider various cybersecurity aspects with the aim to ensure compliance with cybersecurity requirements for a certified cybersecurity and software update management system imposed by the recent United Nations regulations. Automated driving requires increasing networking of vehicles, which in turn expands their attack surface. The security design patterns enable the detection of anomalies in the firmware at boot, ensure secure communication in the vehicle and detect anomalies in in-vehicle communications, prevent unauthorized electronic control units from successfully transmitting messages, provide a way to transmit and aggregate security-related events within a vehicle network, and report to entities external to the vehicle. Using the example of a future high-level automotive Electrical/Electronic architecture, we also describe how these security design patterns can be used to become aware of the current attack situation and to react to it.
|
BibTeX:
@Inbook{Fenzl2023,
author="Fenzl, Florian
and Plappert, Christian
and Rieke, Roland
and Zelle, Daniel
and Costantino, Gianpiero
and De Vincenzi, Marco
and Matteucci, Ilaria",
editor="Dimitrakos, Theo
and Lopez, Javier
and Martinelli, Fabio",
title="Collaborative Security Patterns for Automotive Electrical/Electronic Architectures",
bookTitle="Collaborative Approaches for Cyber Security in Cyber-Physical Systems",
year="2023",
publisher="Springer International Publishing",
address="Cham",
pages="63--97",
isbn="978-3-031-16088-2",
doi="10.1007/978-3-031-16088-2_4",
url="https://doi.org/10.1007/978-3-031-16088-2_4"
}
|
Florian Fenzl, Felix Gail, Lukas Jäger, Christian Plappert, Roland Rieke, Theo Dimitrakos, Ali Hariri, Hussein Joumaa
A Policy-driven Architecture for Security Incident Mitigation in Connected Vehicles, ,
SCIS 2023, 2023 Symposium on Cryptography and Information Security, Fukuoka, Japan, Jan. 24-27, 2023
[Abstract]
|
| Abstract:
With vehicle networks increasing more and more in complexity to enable more advanced
features, such as autonomous driving, their cyberattack surface increases. In order to mitigate upcoming
cyberattacks, more sophisticated and adaptable security approaches are required. Especially
critical is the secure implementation of usage control systems within automotive networks since the
increased communication with external entities provides attackers with new ways to infiltrate the vehicle
network. Modern standard access management systems have difficulty dynamically adapting to new
situations or responding to potential attacks. To improve security and adaptability of usage control
systems, we propose means to integrate additional in-vehicle security measurement and verification
mechanisms, e.g., based on an Intrusion Detection System or Hardware Trust Anchors like Trusted
Platform Modules, with our policy driven usage control system. This allows us to incorporate runtime
and boot-time security incidents into our policy decisions. In addition, we discuss the described system
using some application scenarios for intrusions as an example.
|
BibTeX:
@INPROCEEDINGS{Fenzl2023,
author={Florian Fenzl and Felix Gail and Lukas J\"ager and Christian Plappert and Roland Rieke and Theo Dimitrakos and Ali Hariri and Hussein Joumaa},
booktitle={},
title={A Policy-driven Architecture for Security Incident Mitigation in Connected Vehicles},
year={2023},
month={January}}
|
Clemens Arzt, Steven Kleemann, Christian Plappert, Roland Rieke, and Daniel Zelle
Datenverarbeitung und Cybersicherheit in der Fahrzeugautomatisierung
- Rechtliche und technische Anforderungen im Verbund,
MMR-Beilage, MultiMedia und Recht - Beilage, Heft 7 (Seite 593-614), C.H.Beck, 2022
[Abstract]
[Bibtex]
[Paper ]
[Author version (free access)]
|
| Abstract:
Der Beitrag erörtert ausführlich die neue Rechtslage vor dem Hintergrund des nationalen
und europäischen Datenschutzrechts und den Vorgaben der dazugehörigen
UNECE-Regelungen. Von besonderem Interesse sind in diesem Zusammenhang der
neue § 1g StVG und die in der AFGBV enthaltenen Regelungen für den Betrieb eines
digitalen Datenspeichers sowie die Anforderungen an die Sicherheit im Bereich der
Informationstechnologie bei Datenspeicherung und Datenübermittlung automatisierter
Kraftfahrzeuge. Die hier als relevant identifizierten UNECE-Regelungen 155 (Cybersicherheit)
und 156 (Software-Updates) werden in Folge dieser Neuregelung künftig
einen noch wichtigeren Stellenwert im Automobilbereich einnehmen.
Die an die rechtlichen Ausführungen anschließende technische Analyse in diesem Beitrag
leitet IT- und Datensicherheitsanforderungen sowie beispielhafte Maßnahmen zur
wirkungsvollen Umsetzung ab und vergleicht diese mit den Maßgaben der einschlägigen
UNECE-Regelungen. Dabei wird aufgezeigt, welche technischen Maßnahmen erforderlich
sind, um diesen Anforderungen gerecht zu werden. Die hieraus abgeleiteten
technischen Maßnahmen nehmen Bezug auf die rechtlichen Regelungen und ermöglichen
dadurch einen belastbaren Abgleich von Technik und Recht.
|
BibTeX:
@INPROCEEDINGS{Arzt2022,
author={Clemens Arzt and Steven Kleemann and Christian Plappert and Roland Rieke and Daniel Zelle},
booktitle={MMR-Beilage, MultiMedia und Recht - Beilage, 593},
title={Datenverarbeitung und Cybersicherheit in der Fahrzeugautomatisierung - Rechtliche und technische Anforderungen im Verbund},
year={2022},
month={July},
volume={2022},
number={7},
pages={593-614},
url = {https://beck-online.beck.de/Bcid/Y-300-Z-MMR-BEIL-B-2022-S-593-N-1}}
|
Davide Micale, Gianpiero Costantino, Ilaria Matteucci, Florian Fenzl, Roland Rieke and Giuseppe Patane
CAHOOT: A Context-Aware veHicular intrusiOn detectiOn sysTem,
The 3rd International Workshop on Machine Learning for Trust, Security and Privacy
in Computing and Communications (MLTrustCom 2022)
In conjunction with
The 21st IEEE International Conference on Trust, Security and Privacy in Computing and Communications
(IEEE TrustCom 2022)
[Abstract]
[Bibtex]
[Paper ]
|
| Abstract:
Software in modern vehicles is becoming increasingly
complex and subject to vulnerabilities that an intruder can
exploit to alter the functionality of vehicles. To this purpose, we
introduce CAHOOT, a novel context-aware Intrusion Detection
System (IDS) capable of detecting potential intrusions in both
human and autonomous driving modes. In CAHOOT, context
information consists of data collected at run-time by vehicle's
sensors and engine. Such information is used to determine
drivers' habits and information related to the environment, like
traffic conditions. In this paper, we create and use a dataset by
using a customised version of the MetaDrive simulator capable
of collecting both human and AI driving data. Then we simulate
several types of intrusions while driving: denial of service,
spoofing and replay attacks. As a final step, we use the generated
dataset to evaluate the CAHOOT algorithm by using several
machine learning methods. The results show that CAHOOT is
extremely reliable in detecting intrusions.
|
BibTeX:
@INPROCEEDINGS{Micale2022,
author={Micale, Davide and Costantino, Gianpiero and Matteucci, Ilaria and Fenzl, Florian and Rieke, Roland and Patanè, Giuseppe},
booktitle={2022 IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom)},
title={CAHOOT: a Context-Aware veHicular intrusiOn detectiOn sysTem},
year={2022},
volume={},
number={},
pages={1211-1218},
doi={10.1109/TrustCom56396.2022.00168}}
|
Lucas Buschlinger, Roland Rieke, Sanat Sarda, and Christoph Krauß,
Decision Tree-Based Rule Derivation for Intrusion Detection in Safety-Critical Automotive Systems,
PDP2022, virtual Valladolid Spain, March 09-11 2022
[Abstract]
[Bibtex]
[Paper ]
[Author created version]
|
| Abstract:
Intrusion Detection Systems (IDSs) are being introduced
into safety-critical systems such as connected vehicles.
Since the behavior and effectiveness of measures are validated
before approval, the decisions made by an IDS are required to be
traceable and the IDS also needs to work efficiently on
resource-constrained embedded systems. These requirements complicate
the direct use of Machine Learning (ML) approaches in IDS
design. In this paper, we propose an approach to using ML
to generate rules for an efficient rule-based IDS like Snort.
Our approach eases the time-consuming and difficult process
of creating a rule set. We use decision trees to generate rules
that can be used by experts as a basis for creating a rule set for
a specific safety-critical use case. In addition, we use long short-term
memory methods to circumvent the problem of limited
training data availability, a common limitation in safety-critical
systems. Our implementation and evaluation shows the feasibility
of our approach to derive specific IDS rules for such systems.
|
BibTeX:
@INPROCEEDINGS{Buschlinger2022,
author={Lucas Buschlinger and Roland Rieke and Sanat Sarda and Christoph Krau{\ss}},
booktitle={2022 30th Euromicro International Conference on Parallel, Distributed and Network-Based Processing (PDP)},
title={Decision Tree-Based Rule Derivation for Intrusion Detection in Safety-Critical Automotive Systems},
year={2022},
month={March},
volume={},
number={},
pages={246-254},
doi={10.1109/PDP55904.2022.00046}}
|
Christian Plappert, Florian Fenzl, Roland Rieke, Ilaria Matteucci, Gianpiero Costantino, and Marco De Vincenzi,
SECPAT: Security Patterns for Resilient Automotive E/E Architectures,
PDP2022, virtual Valladolid Spain, March 09-11 2022
[Abstract]
[Bibtex]
[Paper ]
[Author created version]
|
| Abstract:
Automated driving requires increasing networking
of vehicles, which in turn broadens their attack surface. In this
paper, we describe several security design patterns that target
critical steps in automotive attack chains and mitigate their consequences.
These patterns enable the detection of anomalies in the
firmware when booting, detect anomalies in the communication in
the vehicle, prevent unauthorized control units from successfully
transmitting messages, offer a way of transmitting security-related
events within a vehicle network and reporting them to
units external to the vehicle, and ensure that communication in
the vehicle is secure. Using the example of a future high-level
Electrical / Electronic (E / E) architecture, we also describe how
these security design patterns can be used to become aware of
the current attack situation and how to react to it.
|
BibTeX:
@INPROCEEDINGS{Plappert2022,
author={Christian Plappert and Florian Fenzl and Roland Rieke and Ilaria Matteucci and Gianpiero Costantino and Marco De Vincenzi},
booktitle={2022 30th Euromicro International Conference on Parallel, Distributed and Network-Based Processing (PDP)},
title={SECPAT: Security Patterns for Resilient Automotive E/E Architectures},
year={2022},
month={March},
volume={},
number={},
pages={255-264},
doi={10.1109/PDP55904.2022.00047}}
|
Daniel Zelle, Christian Plappert, Roland Rieke, Dirk Scheuermann, and Christoph Krauß,
ThreatSurf: A method for automated Threat Surface assessment in automotive cybersecurity engineering,
Elsevier journal: Microprocessors and Microsystems: Embedded Hardware Design (MICPRO), 2022
[Abstract]
[Bibtex]
[Paper (Open Access)]
|
| Abstract:
Connected smart cars enable new attacks that may have serious consequences. Thus, the development of
new cars must follow a cybersecurity engineering process including a Threat Analysis and Risk Assessment
(TARA). The attack surface assessment is a central aspect of a TARA. In this paper, we introduce a concrete
approach for attack surface assessment following the steps asset identification, threat scenario identification,
attack path analysis, and attack feasibility rating of a TARA compliant to ISO/SAE DIS 21434 and an
approach to automatize them. We define a generic reference architecture and assets constituting the attack
surface, attack building blocks with associated feasibility rating, and a method for automated generation
and rating of attack paths using the attack building blocks and attack feasibility. Our exemplary application
of the automated attack surface assessment on several threats from the UN regulation no. 155 shows the
feasibility of our approach.
|
BibTeX:
@article{Zelle2022,
title = {ThreatSurf: A method for automated Threat Surface assessment in automotive cybersecurity engineering},
author={Daniel Zelle and Christian Plappert and Roland Rieke and Dirk Scheuermann and Christoph Krau{\ss}},
journal = {Microprocessors and Microsystems},
volume = {90},
pages = {104461},
year = {2022},
issn = {0141-9331},
doi = {10.1016/j.micpro.2022.104461},
url = {https://www.sciencedirect.com/science/article/pii/S0141933122000321},
}
|
Yannick Chavalier, Florian Fenzl, Maxim Kolomeets, Roland Rieke, Andrey Chechulin, and Christoph Krauß,
Cyberattack detection in vehicles using characteristic functions, artificial neural networks and visual analysis,
Journal of Informatics and Automation (SPIIRAS Proceedings)
[Abstract]
[Bibtex]
[Paper (Open Access)]
|
| Abstract:
The connectivity of autonomous vehicles induces new attack surfaces and thus the demand for sophisticated cybersecurity management.
Thus, it is important to ensure that in-vehicle network monitoring includes the ability to accurately detect intrusive behavior and analyze cyberattacks from vehicle data and vehicle logs in a privacy-friendly manner.
For this purpose, we describe and evaluate a method that utilizes characteristic functions
and compare it with an approach based on artificial neural networks.
Visual analysis of the respective event streams complements the evaluation.
Although the characteristic functions method is an order of magnitude faster, the accuracy of the results obtained is at least comparable to those obtained with the artificial neural network.
Thus, this method is an interesting option for implementation in in-vehicle embedded systems.
An important aspect for the usage of the analysis methods within a cybersecurity framework is the explainability of the detection results.
|
BibTeX:
@article{Chevalier2021,
title={Cyberattack detection in vehicles using characteristic functions, artificial neural networks, and visual analysis},
volume={20},
url={http://ia.spcras.ru/index.php/sp/article/view/15028},
DOI={10.15622/ia.20.4.4},
number={4},
journal={Informatics and Automation},
author={Chevalier, Yannick and Fenzl, Florian and Kolomeets, Maxim and Rieke, Roland and Chechulin, Andrey and Krau{\ss}, Christoph},
year={2021},
month={Aug.},
pages={845-868}
}
|
Florian Fenzl, Roland Rieke, and Andreas Dominik,
In-vehicle detection of targeted CAN bus attacks,
ARES2021, The 16th International Conference on Availability, Reliability and Security, virtual Vienna Austria August 17 - 20, 2021
[Abstract]
[Bibtex]
[Paper (Open Access)]
|
| Abstract:
Most vehicles use the controller area network bus for communication between their components.
Attackers who have already penetrated the in-vehicle network often
utilize this bus in order to take control of safety-relevant components
of the vehicle.
Such targeted attack scenarios are often hard to detect by
network intrusion detection systems because the specific payload
is usually not contained within their training data sets.
In this work, we describe an intrusion detection system that
uses decision trees that have been modelled through genetic programming.
We evaluate the advantages and disadvantages of this approach
compared to artificial neural networks and rule-based approaches.
For this, we model and simulate specific targeted attacks as well as
several types of intrusions described in the literature.
The results show that the genetic programming approach is well suited
to identify intrusions with respect to complex relationships between sensor
values which we consider important for the classification of specific targeted attacks.
However, the system is less efficient for the classification of other
types of attacks which are better identified by the alternative
methods in our evaluation.
Further research could thus consider hybrid approaches.
|
BibTeX:
@inproceedings{Fenzl2021,
author = {Fenzl, Florian and Rieke, Roland and Dominik, Andreas},
title = {In-Vehicle Detection of Targeted CAN Bus Attacks},
year = {2021},
isbn = {9781450390514},
publisher = {Association for Computing Machinery},
address = {New York, NY, USA},
url = {https://doi.org/10.1145/3465481.3465755},
doi = {10.1145/3465481.3465755},
abstract = { Most vehicles use the controller area network bus for communication between their
components. Attackers who have already penetrated the in-vehicle network often utilize
this bus in order to take control of safety-relevant components of the vehicle. Such
targeted attack scenarios are often hard to detect by network intrusion detection
systems because the specific payload is usually not contained within their training
data sets. In this work, we describe an intrusion detection system that uses decision
trees that have been modelled through genetic programming. We evaluate the advantages
and disadvantages of this approach compared to artificial neural networks and rule-based
approaches. For this, we model and simulate specific targeted attacks as well as several
types of intrusions described in the literature. The results show that the genetic
programming approach is well suited to identify intrusions with respect to complex
relationships between sensor values which we consider important for the classification
of specific targeted attacks. However, the system is less efficient for the classification
of other types of attacks which are better identified by the alternative methods in
our evaluation. Further research could thus consider hybrid approaches.},
booktitle = {The 16th International Conference on Availability, Reliability and Security},
articleno = {32},
numpages = {7},
keywords = {Controller area network security, Machine learning, Intrusion detection, Security monitoring, Automotive security, Anomaly detection, Genetic Programming},
location = {Vienna, Austria},
series = {ARES 2021}
}
|
Christian Plappert, Daniel Zelle, Henry Gadacz, Roland Rieke, Dirk Scheuermann, and
Christoph Krauß,
Attack Surface Assessment for Cybersecurity Engineering in the Automotive Domain,
PDP2021, virtual Valladolid Spain, March 10-12 2021
[Abstract]
[Bibtex]
[Paper ]
[Author created version]
|
| Abstract:
Connected smart cars enable new attacks which may have serious consequences. Thus, the development of new cars must follow a cybersecurity engineering process as defined for example in ISO/SAE 21434. A central part of such a process is the threat and risk assessment including an attack feasibility rating. We present an attack surface assessment with focus on the attack feasibility rating compliant to ISO/SAE 21434. We introduce a reference architecture with assets constituting the attack surface, the attack feasibility rating for these assets, and the application of this rating on typical use cases. The attack feasibility rating assigns attacks and assets to an evaluation of the attacker dimensions and the feasibility of attacks derived from it. We show on sample use cases how this rating can be used to assess the feasibility of an entire attack path. The attack feasibility rating can be used as a building block in a threat and risk assessment according to ISO/SAE 21434.
|
BibTeX:
@INPROCEEDINGS{Plappert2021,
author={Plappert, Christian and Zelle, Daniel and Gadacz, Henry and Rieke, Roland and Scheuermann, Dirk and Krauß, Christoph},
booktitle={2021 29th Euromicro International Conference on Parallel, Distributed and Network-Based Processing (PDP)},
title={Attack Surface Assessment for Cybersecurity Engineering in the Automotive Domain},
year={2021},
volume={},
number={},
pages={266-275},
doi={10.1109/PDP52278.2021.00050}}
|
Diethelm Bienhaus, Andreas Ebner, Lukas Jäger, Roland Rieke, and Christoph Krauß,
Secure Gate: Secure Gateways and Wireless Sensors as Enablers for Sustainability in Production Plants,
Elsevier Journal: Simulation Modelling Practice and Theory, 2021
[Abstract]
[Bibtex]
[Paper (Open Access)]
|
| Abstract:
The Internet of Things has reached the industry. Allowing connectivity from
the shop floor to the Internet requires appropriate security mechanisms to provide
protection against cyber attackers. In this paper, we propose a security
architecture for a gateway connecting sensors and automation components from
production lines with Internet or cloud based systems. A Trusted Platform
Module 2.0 is used for protecting the cryptographic keys used in secure communication
protocols and to provide protection against illegitimate firmware
manipulation. As proof of concept, we implemented the key protection functionality
with a TPM 2.0 for the OPC UA protocol. In a field test, gateways
have been installed together with wireless sensors in production plants. Two
significant results with respect to the sustainability objectives of secure remote
production, namely, reduction of chemical waste and reduction of electrical energy
consumption have been demonstrated.
|
BibTeX:
@article{Bienhaus2021,
author = {Diethelm Bienhaus and Andreas Ebner and Lukas J{\"{a}}ger and Roland Rieke and Christoph Krau{\ss}},
title = {Secure gate: Secure gateways and wireless sensors as enablers for sustainability in production plants},
journal = {Simulation Modelling Practice and Theory},
volume = {109},
pages = {102282},
year = {2021},
issn = {1569-190X},
doi = {https://doi.org/10.1016/j.simpat.2021.102282},
url = {https://www.sciencedirect.com/science/article/pii/S1569190X21000113}
}
|
Florian Fenzl, Roland Rieke, Yannick Chevalier, Andreas Dominik, and Igor Kotenko,
Continuous Fields: Enhanced In-Vehicle Anomaly Detection using Machine Learning Models,
Elsevier Journal: Simulation Modelling Practice and Theory, 2020
[Abstract]
[Bibtex]
[Paper (Open Access)]
|
| Abstract:
The attack surface of a modern vehicle increases with its connectivity.
A strategy to prevent attacks or at least to identify such attacks and
to mitigate their effects is therefore imperative.
The detection of indications for intrusive behavior
in an in-vehicle network is an important aspect of a holistic security concept.
The structure of the payload of in-vehicle messages with respect to
the encoded sensor values is in general confidential.
Therefore, most researchers consider the structure of the in-vehicle messages
to be bit- or byte-fields.
However, this may hide anomalies which are characterized by correlations between
sensor values transferred by the in-vehicle messages.
In this work, we evaluate the influence of accuracy of the model of
the payload structure with respect to the actual sensor values
on the results of different intrusion detection methods.
In particular, we analyze if an improved alignment is helpful
to detect anomalies introduced by stealthy intrusions.
In order to cover conceptually different modeling and reasoning techniques,
we adapted a deep learning approach as well as a characteristic functions based
intrusion detection approach to utilize such message streams.
An important aspect is that the explainability of the results is better compared to
deep learning systems.
We further developed a set of test vectors based on log files of a vehicle
enriched by different intrusions. In particular, we included simulations of stealthy intrusions
which mask certain sensor values within the respective messages.
The effectiveness of the developed methods is demonstrated by various experiments.
|
BibTeX:
@article{Fenzl2020,
author = "Florian Fenzl and Roland Rieke and Yannick Chevalier and Andreas Dominik and Igor Kotenko",
title = "Continuous Fields: Enhanced In-Vehicle Anomaly Detection using Machine Learning Models",
journal = "Simulation Modelling Practice and Theory",
volume = "105",
pages = "102143",
year = "2020",
issn = "1569-190X",
doi = "https://doi.org/10.1016/j.simpat.2020.102143",
url = "http://www.sciencedirect.com/science/article/pii/S1569190X20300824",
keywords = "Controller area network security, Intrusion detection, Anomaly detection, Machine learning, Automotive security, Security monitoring",
}
|
Daniel Zelle, Roland Rieke,Christian Plappert, Christoph Krauß, Dmitry Levshun, and Andrey Chechulin (2020),
SEPAD - Security Evaluation Platform for Autonomous Driving,
PDP2020, virtual Västerås, Sweden, March 11-13, 2020
[Abstract]
[Bibtex]
[Paper]
[Author created version]
|
| Abstract: The development and evaluation of security
solutions for autonomous vehicles is a challenging task. Many
researchers have no access to real vehicles to implement and test
their solutions. In addition, vehicle E/E architectures of
different brands or even model series of one car manufacturer
differ significantly. Also, vehicles may be the source of physical
hazards, e.g., an exploding airbag. To enable researchers to
develop, implement, and evaluate new security solutions for
autonomous vehicles, we propose a new security evaluation platform
called SEPAD and a dedicated development process for testing
security mechanisms with it. SEPAD allows to model realistic E/E
architectures where the developed security solutions can be
integrated and evaluated without causing safety risks for the
researcher or other road users.
|
BibTeX:
@InProceedings{Zelle2020,
author={D. {Zelle} and R. {Rieke} and C. {Plappert} and C. {Krauß} and
D. {Levshun} and A. {Chechulin}},
booktitle={2020 28th Euromicro International Conference on Parallel,
Distributed and Network-Based Processing (PDP)},
title={SEPAD - Security Evaluation Platform for Autonomous Driving},
year={2020},
volume={},
number={},
pages={413-420},
abstract={The development and evaluation of security solutions for
autonomous vehicles is a challenging task. Many researchers have no
access to real vehicles to implement and test their solutions. In
addition, vehicle E/E architectures of different brands or even model
series of one car manufacturer differ significantly. Also, vehicles may
be the source of physical hazards, e.g., an exploding airbag. To enable
researchers to develop, implement, and evaluate new security solutions
for autonomous vehicles, we propose a new security evaluation platform
called SEPAD and a dedicated development process for testing security
mechanisms with it. SEPAD allows to model realistic E/E architectures
where the developed security solutions can be integrated and evaluated
without causing safety risks for the researcher or other road users.},
keywords={Security;Autonomous vehicles;Protocols;Computer
architecture;Automotive engineering;Sensors;Automobiles;automotive
security;evaluation platform;autonomous driving;intrusion
detection;trusted computing;secure in-vehicle protocols},
doi={10.1109/PDP50117.2020.00070},
ISSN={2377-5750},
month={March},
}
|
Yannick Chevalier, Roland Rieke, Florian Fenzl, Andrey Chechulin, and Igor Kotenko (2019),
ECU-Secure: Characteristic Functions for In-Vehicle Intrusion Detection,
IDC2019, St. Petersburg, Russia, October 7-9, 2019 (Springer SCI, volume 868)
[Abstract]
[Bibtex]
[Paper]
[Author created version]
|
| Abstract:
Growing connectivity of vehicles induces increasing attack surfaces
and thus the demand for a sophisticated security strategy.
One part of such a strategy is to accurately detect intrusive behavior in an in-vehicle network.
Therefore, we built a log analyzer in C that focused on payload bytes having either a
small set of different values or a small set of possible changes.
While being an order of magnitude faster, the accuracy of the results obtained is
at least comparable with results obtained using standard machine learning techniques.
These features make this approach an interesting option for implementation within in-vehicle embedded systems.
Another important aspect is that the explainability of the results is better compared to deep learning systems.
|
BibTeX:
@InProceedings{Chevalier2019,
author = {Yannick Chevalier and Roland Rieke and Florian Fenzl and Andrey Chechulin and Igor V. Kotenko},
editor = {Igor V. Kotenko and Costin Badica and Vasily Desnitsky and Didier El Baz and Mirjana Ivanovic},
title="ECU-Secure: Characteristic Functions for In-Vehicle Intrusion Detection",
booktitle="Intelligent Distributed Computing XIII",
series = {Studies in Computational Intelligence},
volume = {868},
publisher = {Springer},
year = {2020},
address="Cham",
pages={495--504},
doi = {10.1007/978-3-030-32258-8\_58},
isbn="978-3-030-32258-8"
}
|
Diethelm Bienhaus, Lukas Jäger, Roland Rieke, and Christoph Krauß (2019),
Gateway for Industrial Cyber-Physical Systems with Hardware-based Trust Anchors,
IDC2019, St. Petersburg, Russia, October 7-9, 2019 (Springer SCI, volume 868)
[Abstract]
[Bibtex]
[Paper]
[Author created version]
|
| Abstract:
Industrial Cyber-Physical Systems require appropriate security mechanisms to provide protection against cyber attackers.
In this paper, we propose a security architecture for a gateway connecting production and cloud systems.
A Trusted Platform Module 2.0 is used for protecting the cryptographic keys used in secure communication protocols and to provide protection against illegitimate firmware manipulation.
As proof of concept, we implemented the key protection functionality with a TPM 2.0 for the OPC UA protocol.
|
BibTeX:
@InProceedings{Bienhaus2019,
author = {Diethelm Bienhaus and Lukas J{\"{a}}ger and Roland Rieke and Christoph Krau{\ss}},
editor = {Igor V. Kotenko and Costin Badica and Vasily Desnitsky and Didier El Baz and Mirjana Ivanovic},
title="Gateway for Industrial Cyber-Physical Systems with Hardware-Based Trust Anchors",
booktitle="Intelligent Distributed Computing XIII",
doi = {10.1007/978-3-030-32258-8\_61},
series = {Studies in Computational Intelligence},
volume = {868},
publisher = {Springer},
year = {2020},
address="Cham",
pages="521--528",
isbn="978-3-030-32258-8"
}
|
Ivo Berger, Roland Rieke, Maxim Kolomeets, Andrey Chechulin, and Igor Kotenko (2018),
Comparative study of machine learning methods for in-vehicle intrusion detection,
Computer Security. ESORICS 2018 International Workshops, CyberICPS 2018 and SECPRE 2018, Barcelona, Spain, September 6-7, 2018, Revised Selected Papers (Springer LNCS 11387)
[Abstract]
[Bibtex]
[Paper]
[Author created version]
|
| Abstract:
An increasing amount of cyber-physical systems within modern cars, such as sensors, actuators, and their electronic control units are connected by in-vehicle networks and these in turn are connected to the evolving Internet of vehicles in order to provide ``smart'' features such as automatic driving assistance. The controller area network bus is commonly used to exchange data between different components of the vehicle, including safety critical systems as well as infotainment. As every connected controller broadcasts its data on this bus it is very susceptible to intrusion attacks which are enabled by the high interconnectivity and can be executed remotely using the Internet connection.
This paper aims to evaluate relatively simple machine learning methods as well as deep learning methods and develop adaptations to the automotive domain in order to determine the validity of the observed data stream and identify potential security threats.
|
BibTeX:
@InProceedings{Berger2019,
author="Berger, Ivo
and Rieke, Roland
and Kolomeets, Maxim
and Chechulin, Andrey
and Kotenko, Igor",
editor="Katsikas, Sokratis K.
and Cuppens, Fr{\'e}d{\'e}ric
and Cuppens, Nora
and Lambrinoudakis, Costas
and Ant{\'o}n, Annie
and Gritzalis, Stefanos
and Mylopoulos, John
and Kalloniatis, Christos",
title="Comparative Study of Machine Learning Methods for In-Vehicle Intrusion Detection",
booktitle="Computer Security. ESORICS 2018 International Workshops, CyberICPS 2018 and SECPRE 2018, Barcelona, Spain, September 6-7, 2018, Revised Selected Papers",
year="2019",
publisher="Springer",
address="Cham",
pages="85--101",
abstract="An increasing amount of cyber-physical systems within modern cars, such as sensors, actuators, and their electronic control units are connected by in-vehicle networks and these in turn are connected to the evolving Internet of vehicles in order to provide ``smart'' features such as automatic driving assistance. The controller area network bus is commonly used to exchange data between different components of the vehicle, including safety critical systems as well as infotainment. As every connected controller broadcasts its data on this bus it is very susceptible to intrusion attacks which are enabled by the high interconnectivity and can be executed remotely using the Internet connection. This paper aims to evaluate relatively simple machine learning methods as well as deep learning methods and develop adaptations to the automotive domain in order to determine the validity of the observed data stream and identify potential security threats.",
isbn="978-3-030-12786-2",
series = {Lecture Notes in Computer Science},
volume = {11387},
doi = {10.1007/978-3-030-12786-2_6},
}
|
Roland Rieke, Marc Seidemann, Elise Kengni Talla, Daniel Zelle, and Bernhard Seeger (2017),
Behavior Analysis for Safety and Security in Automotive Systems,
The 25th Euromicro International Conference on Parallel, Distributed and Network-based Computing (PDP 2017)
[Abstract]
[Bibtex]
[Paper]
[Author's version]
[Readme (data used in the paper)]
[Data used in the paper]
|
| Abstract:
The connection of automotive systems with other systems such as
road-side units, other vehicles, and various servers in the Internet
opens up new ways for attackers to remotely access safety relevant
subsystems within connected cars. The security of connected cars
and the whole vehicular ecosystem is thus of utmost importance for
consumer trust and acceptance of this emerging technology. This
paper describes an approach for on-board detection of unanticipated
sequences of events in order to identify suspicious activities. The
results show that this approach is fast enough for in-vehicle
application at runtime. Several behavior models and synchronization
strategies are analyzed in order to narrow down suspicious sequences
of events to be sent in a privacy respecting way to a global
security operations center for further in-depth analysis.
|
BibTeX:
@INPROCEEDINGS{pdp2017,
booktitle={Parallel, Distributed and Network-Based Processing (PDP), 2017 25nd Euromicro International Conference on},
author={Roland Rieke and Marc Seidemann and Elise Kengni Talla and Daniel Zelle and Bernhard Seeger},
title={Behavior Analysis for Safety and Security in Automotive Systems},
year={2017},
month={Mar},
pages={381-385},
keywords={automotive security; connected car; predictive security analysis;
security modeling and simulation; security monitoring;
complex event processing; process discovery},
doi={10.1109/PDP.2017.67},
url={http://ieeexplore.ieee.org/document/7912675/},
publisher = {IEEE Computer Society},
}
|
Andre Rein, Roland Rieke, Michael Jäger, Nicolai Kuntze, and Luigi Coppolino (2015),
Trust Establishment in Cooperating Cyber-Physical Systems,
Security of Industrial Control Systems and Cyber Physical Systems: First Workshop, CyberICS 2015 and First Workshop, WOS-CPS 2015 Vienna, Austria, September 21--22, 2015 Revised Selected Papers (Springer LNCS 9588)
[Abstract]
[Bibtex]
[Paper]
[Author's pre-proceedings version]
|
| Abstract:
Cooperating systems are systems of systems that collaborate for a
common purpose. In this work, we consider networked cooperating
systems that base important decisions on data gathered from external
sensors and use external actuators to enforce safety
critical actions.
Typical examples of cooperating cyber-physical systems are
critical infrastructure process control systems. Such systems must
not only be secure, they must be demonstrably so.
Using the example of a hydroelectric power plant control system,
this paper analyzes security threats for networked cooperating
systems, where sensors providing decision critical data are
placed in non-protected areas and thus are exposed to various kinds
of attacks.
We propose a concept for trust establishment in cyber-physical
cooperating systems. Using trusted event reporting for critical
event sources, the authenticity of the security related events can
be verified. Based on measurements obtained with a prototypical
realisation, we evaluate and analyze the amount of overhead data
transmission between event source and data verification system
needed for trust establishment. We propose an efficient
synchronisation scheme for system integrity data, reducing network
traffic as well as verification effort.
|
BibTeX:
@Inbook{Rein2016,
author="Rein, Andre
and Rieke, Roland
and J{\"a}ger, Michael
and Kuntze, Nicolai
and Coppolino, Luigi",
editor="B{\'e}cue, Adrien
and Cuppens-Boulahia, Nora
and Cuppens, Fr{\'e}d{\'e}ric
and Katsikas, Sokratis
and Lambrinoudakis, Costas",
title="Trust Establishment in Cooperating Cyber-Physical Systems",
bookTitle="Security of Industrial Control Systems and Cyber Physical Systems: First Workshop, CyberICS 2015 and First Workshop, WOS-CPS 2015 Vienna, Austria, September 21--22, 2015 Revised Selected Papers",
year="2016",
publisher="Springer International Publishing",
address="Cham",
pages="31--47",
isbn="978-3-319-40385-4",
doi="10.1007/978-3-319-40385-4_3",
series={Lecture Notes in Computer Science},
volume={9588},
url="http://dx.doi.org/10.1007/978-3-319-40385-4_3"
}
|
Roland Rieke, Maria Zhdanova, and Jürgen Repp (2015),
Security and Business Situational Awareness,
Cyber Security and Privacy, 4th Cyber Security and Privacy Innovation Forum, CSP Innovation Forum 2015
[Abstract]
[Bibtex]
[Paper]
[Author's version]
|
| Abstract:
"Security needs to be aligned with business".
Business situational awareness is the ability to continually monitor
ongoing actions and events related to business operations
and estimate the immediate and close-future impact of the new information.
This ability is crucial for business continuity and should encompass all associated aspects.
Considering the growing dependability of businesses on IT on the one hand,
and ever increasing threats on the other,
IT security aspects should get adequate attention in the awareness system.
We present an approach to raise business situational awareness using
an advanced method of predictive security analysis at runtime.
It continually observes a system's event stream to find deviations from specified
behavior and violations of security compliance rules.
Operational models of the key processes
are utilized to
predict critical security states, evaluate possible countermeasures, and
trigger corrective actions.
A security information model maintains
the security strategy and explains possible deviations from the originating goal.
The approach is demonstrated on an industrial scenario from a European research project.
|
BibTeX:
@incollection{RZR-CSP2015,
author={Rieke, Roland and Zhdanova, Maria and Repp, J\"urgen},
title={Security and Business Situational Awareness},
year={2015},
isbn={978-3-319-25359-6},
booktitle={Cyber Security and Privacy},
volume={530},
series={Communications in Computer and Information Science},
editor={Cleary, Frances and Felici, Massimo},
doi={10.1007/978-3-319-25360-2_9},
url={http://dx.doi.org/10.1007/978-3-319-25360-2_9},
publisher={Springer International Publishing},
keywords={Predictive security analysis; Process behavior analysis; Security modeling and simulation; Security monitoring; Security strategy; Security information and event management; Governance and compliance},
pages={103-115},
language={English}
}
|
Roland Rieke, Maria Zhdanova, and Jürgen Repp (2015),
Security Compliance Tracking of Processes in Networked Cooperating Systems,
Journal of Wireless Mobile Networks, Ubiquitous Computing,
and Dependable Applications (JoWUA), Vol. 6, No. 2, 2015
[Abstract]
[BibTeX]
[Paper (free access)]
|
| Abstract:
Systems of systems that collaborate for a common purpose are called
cooperating systems. Typical examples of novel cooperating systems
are electronic health systems and electronic money transfer systems
but also critical infrastructures, such as future vehicular ad hoc
networks and distributed air traffic management systems. Business
processes and technical workflows control the cooperation of
the networked systems. Important safety and security goals of the
applications, business goals, and external compliance requirements
create security obligations for such processes. These processes
must not only be secure, they must be demonstrably so. To support
this, we present an approach for security compliance tracking of
processes in networked cooperating systems using an advanced method
of predictive security analysis at runtime. At that, operational
models are utilized for: (a) tracking conformance of process
behavior with respect to the specification, (b) detection of
behavior anomalies which indicate possible attacks, (c) tracking
compliance of process behavior with respect to safety and security
requirements, and (d) prediction of possible violations of safety
and security policies in the near future. We provide an extensive
background analysis, introduce the model-based conformance
tracking and uncertainty management algorithm, and describe
security compliance tracking and model-based behavior prediction.
We demonstrate the implementation of the proposed approach on a
critical infrastructure scenario from a European research project.
|
BibTeX:
@ARTICLE{jowua15-6-2-02,
Author = {Roland Rieke and Maria Zhdanova and J\"urgen Repp},
title = {Security Compliance Tracking of Processes in Networked Cooperating Systems},
journal = {Journal of Wireless Mobile Networks, Ubiquitous Computing, and Dependable Applications (JoWUA)},
volume = {6},
number = {2},
year = {2015},
month = {June},
pages = {21--40},
ee = {http://isyou.info/jowua/papers/jowua-v6n2-2.pdf}
}
|
Roland Rieke (2014),
Security Analysis of System Behaviour - From 'Security by Design' to 'Security at Runtime' -,
PhD thesis at Philipps-Universität Marburg
[Abstract]
[BibTeX]
[Überblick]
[Info]
[Dissertation (free access, 11 MB)]
|
| Abstract:
The Internet today provides the environment for novel applications and
processes which may evolve way beyond pre-planned scope and
purpose. Security analysis is growing in complexity with the increase
in functionality, connectivity, and dynamics of current electronic
business processes. Technical processes within critical
infrastructures also have to cope with these developments. To tackle
the complexity of the security analysis, the application of models is
becoming standard practice. However, model-based support for security
analysis is not only needed in pre-operational phases but also during
process execution, in order to provide situational security awareness
at runtime.
This cumulative thesis provides three major contributions to modelling
methodology.
Firstly, this thesis provides an approach for model-based analysis and
verification of security and safety properties in order to support
fault prevention and fault removal in system design or redesign.
Furthermore, some construction principles for the design of
well-behaved scalable systems are given.
The second topic is the analysis of the exposition of vulnerabilities
in the software components of networked systems to exploitation by
internal or external threats. This kind of fault forecasting allows
the security assessment of alternative system configurations and
security policies. Validation and deployment of security policies
that minimise the attack surface can now improve fault tolerance and
mitigate the impact of successful attacks.
Thirdly, the approach is extended to runtime applicability. An
observing system monitors an event stream from the observed system
with the aim to detect faults - deviations from the specified
behaviour or security compliance violations - at runtime.
Furthermore, knowledge about the expected behaviour given by an
operational model is used to predict faults in the near
future. Building on this, a holistic security management strategy is
proposed. The architecture of the observing system is described and
the applicability of model-based security analysis at runtime is
demonstrated utilising processes from several industrial scenarios.
The results of this cumulative thesis are provided by 19 selected
peer-reviewed papers.
|
BibTeX:
@PHDTHESIS{drr2014,
author = {Roland Rieke},
title = {{Security Analysis of System Behaviour - From 'Security by Design' to 'Security at Runtime' -}},
url = {http://archiv.ub.uni-marburg.de/diss/z2014/0499},
doi={10.17192/z2014.0499},
school = {Philipps-Universit\"at Marburg, Germany},
year = {2014},
month={Dec}
}
|
Peter Ochsenschläger and Roland Rieke (2014),
Safety by Construction: Well-behaved Scalable Systems,
International Journal On Advances in Systems and Measurements, vol 7, no 3&4, 2014
[Abstract]
[BibTeX]
[Journal (free access)]
[Author's version]
|
| Abstract: This paper presents a formal framework that
provides construction principles for well-behaved scalable
systems, such that starting with a prototype system satisfying
a desired safety property result in a scalable system satisfying a
corresponding safety property, called scalable safety
property. With respect to different aspects of scalability,
the focus of this work is on property preserving structural
scalability. At that, we consider systems composed of a
varying set of individual components where individual components
of the same type behave in the same manner, which is
characteristic for the type. The respective properties can rely
on specific component types and a specific number of individual
components but not on the specific individuality of the
components. Well-behaved scalable systems are characterised by
those systems which fulfil such a kind of property if already one
prototype system (depending on the property) fulfils that
property. Sufficient conditions to specify a certain kind of basic
well-behaved scalable systems are given and it is shown, how to
construct more complex systems by the composition of several
synchronisation conditions. Scalable safety properties can be
used to express privacy policies as well as security and
dependability requirements. It is demonstrated, how the
parameterised problem of verifying such a property is reduced to a
finite state problem for well-behaved scalable systems. The
formal framework for well-behaved scalable systems is developed in
terms of prefix closed formal languages and alphabetic language
homomorphisms.
|
BibTeX:
@article{SysMea14,
author={Peter Ochsenschl\"ager and Roland Rieke},
title={Safety by Construction: Well-behaved Scalable Systems},
year={2014},
journal = "International Journal On Advances in Systems and Measurements",
volume = "7",
number = "3 \& 4",
pages = "239 - 257",
issn = "1942-261x",
publisher = {IARIA}
}
|
Maria Zhdanova, Jürgen Repp, Roland Rieke, Chrystel Gaber, and Baptiste Hemery (2014),
No Smurfs: Revealing Fraud Chains in Mobile Money Transfers,
ARES 2014 (Best Paper Session)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract: Mobile Money Transfer (MMT) services provided
by mobile network operators enable funds transfers made on mobile
devices of end-users, using digital equivalent of cash (electronic
money) without any bank accounts involved. MMT simplifies banking
relationships and facilitates financial inclusion, and, therefore,
is rapidly expanding all around the world, especially in
developing countries. MMT systems are subject to the same controls
as those required for financial institutions, including the
detection of Money Laundering (ML) a source of concern for MMT
service providers. In this paper we focus on an often practiced ML
technique known as micro-structuring of funds or smurfing and
introduce a new method for detection of fraud chains in MMT
systems. Whereas classical detection methods are based on machine
learning and data mining, this work builds on Predictive Security
Analysis at Runtime (PSA@R), a model-based approach for
event-driven process analysis. We provide an extension to PSA@R
which allows us to identify fraudsters in an MMT service
monitoring network behavior of its end-users. We evaluate our
method on simulated transaction logs, containing approximately
460,000 transactions for 10,000 end-users, and compare it with
classical fraud detection approaches. With 99.81% precision and
90.18% recall, we achieve better recognition performance in
comparison with the state of the art.
|
BibTeX:
@incollection{ares2014,
author={Maria Zhdanova and J\"urgen Repp and Roland Rieke and Chrystel Gaber and Baptiste Hemery},
title={No Smurfs: Revealing Fraud Chains in Mobile Money Transfers},
year={2014},
booktitle={Proceedings of 2014 International Conference on Availability, Reliability and Security, ARES 2014},
pages={11-20},
isbn={978-1-4799-4223-7/14},
doi={10.1109/ARES.2014.10},
publisher = {IEEE Computer Society},
}
|
Roland Rieke, Maria Zhdanova, Jürgen Repp, Romain Giot, and Chrystel Gaber (2014),
Verhaltensanalyse zur Erkennung von Missbrauch mobiler Geldtransferdienste,
GI Sicherheit 2014, Lecture Notes in Informatics P-228
[Abstract]
[BibTeX]
[Paper (free access)]
[Author's version]
|
| Abstract:
Die fortlaufende Überwachung von Transaktionen auf Geldwäscheverdacht
ist Finanzinstituten in Deutschland und anderen Ländern vorgeschrieben.
Smurfing ist eine Form der Geldwäsche, bei der durch den Transfer
vieler kleiner Geldbeträge auf unterschiedlichen Wegen mit der Hilfe von
Strohmännern ein hoher Geldbetrag unauffällig transferiert werden soll.
In dieser Arbeit betrachten wir das Smurfing-Risiko im Rahmen
mobiler Geldtransferdienste.
Insbesondere beschreiben wir eine Methode zur vorbeugenden Sicherheitsanalyse zur Laufzeit,
welche das Prozessverhalten in einem Geldtransfer-Service in Bezug auf Transaktionen beobachtet
und versucht, es mit dem erwarteten Verhalten zu vergleichen, welches durch ein Prozessmodell
vorgegeben ist.
Wir analysieren Abweichungen von der vorgegebenen Verhaltensspezifikation auf Anomalien,
die einen möglichen Missbrauch des Finanzdienstes durch Geldwäscheaktivitäten anzeigen.
Wir bewerten die Anwendbarkeit der Vorgehensweise und
beschreiben Messungen der Rechen- und Erkennungsleistung eines prototypischen Werkzeugs
basierend auf realen und simulierten Betriebsprotokollen.
Das Ziel der Experimente ist es, basierend auf Eigenschaften des realen
Finanzdienstes, Missbrauchsmuster in synthetisiertem Prozessverhalten
mit eingefügten Geldwäscheaktivitäten zu erkennen.
|
BibTeX:
@inproceedings{gi2014,
author={Roland Rieke and Maria Zhdanova and J\"urgen Repp and Romain Giot and Chrystel Gaber},
editor= {Stefan Katzenbeisser and Volkmar Lotz and Edgar Weippl},
location={Wien},
booktitle = {GI Sicherheit 2014},
title={{Verhaltensanalyse zur Erkennung von Missbrauch mobiler Geldtransferdienste}},
month={March},
year={2014},
series = {Lecture Notes in Informatics (LNI) -- Proceedings},
isbn= {978-3-88579-622-0},
volume={P-228},
pages={271-282},
url = {http://subs.emis.de/LNI/Proceedings/Proceedings228/article31.html},
publisher={GI}
}
|
Peter Ochsenschläger and Roland Rieke (2014),
Construction Principles for Well-behaved Scalable Systems,
The Ninth International Conference on Systems (ICONS 2014)
[Abstract]
[BibTeX]
[Paper (free access)]
[Author's version]
[Proofs]
|
| Abstract:
We formally define scalable systems as uniformly
monotonic parameterised systems and motivate this definition.
With respect to such scalable systems, we focus on properties, which
rely on specific component types and a specific number of individual
components for these component types but not on the specific
individuality of the individual components. We characterise
well-behaved scalable systems by those systems which fulfil
such a kind of property if already one prototype system (depending
on the property) fulfils that property. Self-similar uniformly
monotonic parameterised systems have the above desired property.
Therefore, we define well-behaved scalable systems as self-similar
scalable systems. This paper presents a formal framework that
provides construction principles for well-behaved scalable systems.
It gives sufficient conditions to specify a certain kind of basic
well-behaved scalable systems and shows how to construct more
complex systems by the composition of several synchronisation
conditions.
|
BibTeX:
@incollection{ochsenschlaeger:rieke:2014,
author = {Peter Ochsenschl\"ager and Roland Rieke},
title = {{Construction Principles for Well-behaved Scalable Systems}},
booktitle = {ICONS 2014, The Ninth International Conference on Systems, February 23 - 27, 2014 - Nice, France},
url="http://www.thinkmind.org/download.php?articleid=icons_2014_2_30_40160",
pages="32-39",
issn="2308-4243",
isbn="978-1-61208-319-3",
publisher={IARIA},
year = {2014}
}
|
Roland Rieke, Jürgen Repp, Maria Zhdanova, and Jörn Eichler (2014),
Monitoring Security Compliance of Critical Processes,
The 22th Euromicro International Conference on Parallel, Distributed and Network-Based Computing (PDP 2014)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract:
Enforcing security in process-aware information systems
at runtime requires the monitoring of systems'
operation using process information. Analysis of this information with
respect to security and compliance aspects is growing in complexity
with the increase in functionality, connectivity, and dynamics of
process evolution.
To tackle this complexity, the application of models is becoming standard
practice. Considering today's frequent changes to processes,
model-based support for security and compliance analysis is not
only needed in pre-operational phases but also at runtime.
This paper presents an approach to support evaluation of
the security status of processes at runtime.
The approach is based on operational formal models derived from
process specifications and security policies comprising technical,
organizational, regulatory and cross-layer aspects.
A process behavior model is synchronized by events from the running process and
utilizes prediction of expected close-future states to find possible
security violations and allow early decisions on countermeasures.
The applicability of the approach is exemplified by a misuse case scenario from a
hydroelectric power plant.
|
BibTeX:
@INPROCEEDINGS{pdp2014,
author={Rieke, Roland and Repp, J\"urgen and Zhdanova, Maria and Eichler, J\"orn},
booktitle={Parallel, Distributed and Network-Based Processing (PDP), 2014 22nd Euromicro International Conference on},
title={Monitoring Security Compliance of Critical Processes},
year={2014},
month={Feb},
pages={552-560},
keywords={critical infrastructures;predictive security analysis;process behavior analysis;security information and event management;security modeling and simulation;security monitoring},
doi={10.1109/PDP.2014.106},
ISSN={1066-6192},
url = {http://ieeexplore.ieee.org/xpl/articleDetails.jsp?arnumber=6787328},
publisher = {IEEE Computer Society},
}
|
Md. Aquil Khan, Mohua Banerjee, and Roland Rieke (2014),
An update logic for information systems,
International Journal of Approximate Reasoning 2014
[Abstract]
[BibTeX]
[Paper]
|
| Abstract:
Updates in a knowledge base, given as an information system in rough set
theory, may need to be made due to changes in (i) the set of attributes, (ii)
attribute-values, or (iii) the set of objects (instances). In this article, we propose
a logic for information systems which incorporates all these three aspects of
updates. The logic can capture the flow of information as well as its effects on
the approximations of concepts. A sound and complete deductive system for
the logic is presented. The decidability issue is also discussed.
|
BibTeX:
@article{Khan2014436,
title = "An update logic for information systems ",
journal = "International Journal of Approximate Reasoning ",
volume = "55",
number = "1, Part 4",
pages = "436 - 456",
year = "2014",
note = "Rough Sets and Logic ",
issn = "0888-613X",
doi = "http://dx.doi.org/10.1016/j.ijar.2013.07.007",
url = "http://www.sciencedirect.com/science/article/pii/S0888613X13001667",
author = "Md. Aquil Khan and Mohua Banerjee and Roland Rieke",
keywords = "Information system",
keywords = "Lower and upper approximations",
keywords = "Modal logic",
keywords = "First order predicate logic "
}
|
Roland Rieke, Maria Zhdanova, Jürgen Repp, Romain Giot, and Chrystel Gaber (2013),
Fraud Detection in Mobile Payment Utilizing Process Behavior Analysis,
RaSIEM 2013 at ARES 2013
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract:
Generally, fraud risk implies any intentional deception made for
financial gain. In this paper, we consider this risk in the field of
services which support transactions with electronic money.
Specifically, we apply a tool for predictive security analysis at runtime
which observes process behavior with respect to transactions
within a money transfer service and tries to match it with expected behavior
given by a process model. We analyze deviations from the given
behavior specification for anomalies that indicate a possible misuse
of the service related to money laundering activities.
We evaluate the applicability of the
proposed approach and
provide measurements on computational and recognition performance of
the tool - Predictive Security Analyser (PSA) - produced using real operational and simulated logs.
The goal of the experiments is to detect misuse patterns reflecting a given money
laundering scheme in synthetic process behavior based on properties
captured from real world transaction events.
|
BibTeX:
@incollection{rasiem2013,
author={Roland Rieke and Maria Zhdanova and J\"urgen Repp and Romain Giot and Chrystel Gaber},
title={Fraud Detection in Mobile Payment Utilizing Process Behavior Analysis},
year={2013},
booktitle={Proceedings of 2013 International Conference on Availability, Reliability and Security, ARES 2013},
pages={662-669},
isbn={978-0-7695-5008-4},
doi={10.1109/ARES.2013.87},
publisher = {IEEE Computer Society},
}
|
Julian Schütte, Roland Rieke, and Timo Winkelvos (2012),
Model-based Security Event Management,
MMM-ACNS 2012, (Springer LNCS 7531)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract:
With the growing size and complexity of current ICT
infrastructures, it becomes increasingly challenging to gain an overview of
potential security breaches. Security Information and Event Management systems
which aim at collecting, aggregating and processing security-relevant
information are therefore on the rise. However, the event model of current
systems mostly describes network events and their correlation, but is not
linked to a comprehensive security model, including system state, security and
compliance requirements, countermeasures, and affected assets. In this paper we
introduce a comprehensive semantic model for security event management. Besides
the description of security incidents, the model further allows to add
conditions over the system state, define countermeasures, and link to external
security models.
|
BibTeX:
@incollection{mmm-acnsa:2012,
author={Sch\"utte, Julian and Rieke, Roland and Winkelvos, Timo},
title={Model-Based Security Event Management},
year={2012},
isbn={978-3-642-33703-1},
booktitle={Computer Network Security},
volume={7531},
series={Lecture Notes in Computer Science},
editor={Kotenko, Igor and Skormin, Victor},
doi={10.1007/978-3-642-33704-8_16},
url={http://dx.doi.org/10.1007/978-3-642-33704-8_16},
publisher={Springer Berlin Heidelberg},
keywords={security strategy meta model; security information and event management; complex event processing},
pages={181-190}
}
|
Roland Rieke, Luigi Coppolino, Andrew Hutchison, Elsa Prieto, and Chrystel Gaber (2012),
Security and Reliability Requirements for Advanced Security Event Management,
MMM-ACNS 2012, (Springer LNCS 7531)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract:
This paper addresses security information management in complex application scenarios. Security Information and Event Management (SIEM) systems collect and examine security related events, with the goal of providing a unified view of the monitored systems' security status. While various SIEMs are in production, there is scope to extend the capability and resilience of these systems. The use of SIEM technology in four disparate scenario areas is used in this paper as a catalyst for the development and articulation of Security and Reliability requirements for advanced security event management. The scenarios relate to infrastructure management for a large real-time sporting event, a mobile money payment system, a managed services environment and a cyber-physical dam control system. The diversity of the scenarios enables elaboration of a comprehensive set of Security and Reliability requirements which can be used in the development of future SIEM systems.
|
BibTeX:
@incollection{mmm-acnsb:2012,
year={2012},
isbn={978-3-642-33703-1},
booktitle={Computer Network Security},
volume={7531},
series={Lecture Notes in Computer Science},
editor={Kotenko, Igor and Skormin, Victor},
doi={10.1007/978-3-642-33704-8_15},
title={Security and Reliability Requirements for Advanced Security Event Management},
url={http://dx.doi.org/10.1007/978-3-642-33704-8_15},
publisher={Springer Berlin Heidelberg},
keywords={security requirements; security information and event management; SIEM; architecting trustworthy systems},
author={Rieke, Roland and Coppolino, Luigi and Hutchison, Andrew and Prieto, Elsa and Gaber, Chrystel},
pages={171-180}
}
|
Roland Rieke, Julian Schütte, and Andrew Hutchison (2012),
Architecting a Security Strategy Measurement and Management System,
MDSec 2012, Proceedings of the Workshop on Model-Driven Security, ACM 2012
[Abstract]
[BibTeX]
[Paper ACM DL]
[Conference Version (free access)]
[Author's version]
|
| Abstract:
The use of formal models to guide security design is appealing. This
paper presents a model driven approach whereby security systems in
operation can be assessed and measured against various requirements
that are defined when the system is created. By aligning with
organisational policy, and business requirements of a specific
system, design and operation can proceed in a way that allows
measurement of how successfully security objectives are being
achieved.
This paper describes a model driven approach which overcomes the
contextual restrictions of existing solutions. In particular, where
models have been used previously these have tended to be predefined
and closed models, whereas the approach described here is an
extensible model that comprises all parts of the security monitoring
and decision support process.
By means of interlinked semantic concepts, the proposed security
strategy meta model provides a way to model security directives at
an abstract level, which can be automatically compiled into specific
rules for an underlying framework of monitoring, decision support,
and enforcement engines.
|
BibTeX:
@inproceedings{MDSec:2012,
author = {Rieke, Roland and Sch\"{u}tte, Julian and Hutchison, Andrew},
title = {Architecting a security strategy measurement and management system},
booktitle = {Proceedings of the Workshop on Model-Driven Security},
series = {MDsec '12},
year = {2012},
isbn = {978-1-4503-1806-8},
location = {Innsbruck, Austria},
pages = {2:1--2:6},
articleno = {2},
numpages = {6},
url = {http://doi.acm.org/10.1145/2422498.2422500},
doi = {10.1145/2422498.2422500},
acmid = {2422500},
publisher = {ACM},
address = {New York, NY, USA},
keywords = {decision support, governance and compliance, information security measurement model, security information and event management, security monitoring, security strategy},
}
|
Roland Rieke, Elsa Prieto, Rodrigo Diaz, Herve Debar, and Andrew Hutchison (2012),
Challenges for Advanced Security Monitoring - The MASSIF
project,
TrustBus 2012, (Springer LNCS 7449)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract:
The vision of creating a next-generation Security Information and
Event Management environment drives the development of an
architecture which provides for trustworthy and resilient
collection of security events from source systems, processes and applications.
A number of novel inspection and analysis techniques are applied to
the events collected to provide high-level situational
security awareness, not only on the network level but also at the
service level where high-level threats such as money laundering
appear. An anticipatory impact analysis will predict the
outcome of threats and mitigation strategies and thus enable
proactive and dynamic response.
|
BibTeX:
@incollection {trustbus:2012,
author = {Rieke, Roland and Prieto, Elsa and Diaz, Rodrigo and Debar, Herv{\'e} and Hutchison, Andrew},
affiliation = {Fraunhofer Institute SIT, Darmstadt, Germany},
title = {Challenges for Advanced Security Monitoring -- The MASSIF Project},
booktitle = {Trust, Privacy and Security in Digital Business},
series = {Lecture Notes in Computer Science},
editor = {Fischer-H\"ubner, Simone and Katsikas, Sokratis and Quirchmayr, Gerald},
publisher = {Springer Berlin / Heidelberg},
isbn = {978-3-642-32286-0},
keyword = {Computer Science},
pages = {222-223},
volume = {7449},
url = {http://dx.doi.org/10.1007/978-3-642-32287-7_23},
doi = {10.1007/978-3-642-32287-7_23},
year = {2012}
}
|
Elsa Prieto, Rodrigo Diaz, Luigi Romano, Roland Rieke, and Mohammed Achemlal (2012),
MASSIF: A Promising Solution to Enhance Olympic Games IT Security,
Global Security, Safety and Sustainability & e-Democracy, (Springer LNICST 99)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract:
Nowadays, Olympic Games have become one of the most profitable
global media events, becoming at the same way more and more attractive target
from the terrorist perspective due to their media diffusion and international
dimension. Critical for the success of such a highly visible event is protecting
and securing the business and the supporting cyber-infrastructure enabling it. In
this context, the MASSIF project aims to provide a new generation SIEM
framework for service infrastructures supporting intelligent, scalable, and
multi-level/multi-domain security event processing and predictive security
monitoring.
|
BibTeX:
@incollection {pdrra:2012,
author = {Prieto, Elsa and Diaz, Rodrigo and Romano, Luigi and Rieke, Roland and Achemlal, Mohammed},
affiliation = {Atos Research and Innovation (ARI), Atos Origin, Europe},
title = {MASSIF: A Promising Solution to Enhance Olympic Games IT Security},
booktitle = {Global Security, Safety and Sustainability \& e-Democracy},
series = {Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering},
editor = {Georgiadis, Christos K. and others},
publisher = {Springer Berlin Heidelberg},
isbn = {978-3-642-33447-4},
keyword = {Computer Science},
pages = {139-147},
volume = {99},
url = {http://dx.doi.org/10.1007/978-3-642-33448-1_20},
doi = {10.1007/978-3-642-33448-1_20},
year = {2012}
}
|
Luigi Coppolino, Michael Jäger, Nicolai Kuntze, and Roland Rieke (2012),
A Trusted Information Agent for Security Information and Event Management,
The Seventh International Conference on Systems (ICONS 2012)
[Abstract]
[BibTeX]
[Paper (free access)]
[Author's version]
|
| Abstract:
This paper addresses security information management in untrusted environments. A security information and event management system collects and examines security related events and provides a unifying view of the monitored system's security status. The sensors, which provide the event data, are typically placed in a non-protected environment at the boarder of the managed system.
They are exposed to various kinds of attacks. Compromised sensors may lead to misjudgement on the system's state with possibly serious consequences. The particular security requirements arising from these problems are discussed for large scale critical infrastructures.
The main contribution of this paper is a concept that provides trusted event reporting. Critical event sources are holistically protected such that authenticity of the security related events is guaranteed. This enables better assessment of the managed system's reliability and trustworthiness.
As a proof of this concept, the paper presents an exemplary realisation of a trustworthy event source.
|
BibTeX:
@incollection{cjkr:2012,
author = {Luigi Coppolino and Michael J\"ager and Nicolai Kuntze and Roland Rieke},
title = {{A Trusted Information Agent for Security Information and Event Management}},
booktitle = {ICONS 2012, The Seventh International Conference on Systems, February 29 - March 5, 2012 - Saint Gilles, Reunion Island},
pages = {6-12},
url = {http://www.thinkmind.org/download.php?articleid=icons_2012_1_20_20062},
publisher={IARIA},
isbn={978-1-61208-184-7},
year = {2012}
}
|
Peter Ochsenschläger and Roland Rieke (2012),
Reliability Aspects of Uniformly Parameterised Cooperations,
The Seventh International Conference on Systems (ICONS 2012)
[Abstract]
[BibTeX]
[Paper (free access)]
[Author's version]
|
| Abstract:
In this paper, we examine reliability aspects of systems, which are
characterised by the composition of a set of identical components.
These components interact in a uniform manner, described by the
schedules of the partners. Such kind of interaction is typical for
scalable complex systems with cloud or grid structure. We call
these systems ``uniformly parameterised cooperations''. We consider
reliability of such systems in a possibilistic sense. This is
formalised by always-eventually properties, a special class of
liveness properties using a modified satisfaction relation, which
expresses possibilities. As a main result, a finite state
verification framework for uniformly parameterised reliability
properties is given. The keys to this framework are structuring
cooperations into phases and defining closed behaviours of systems.
In order to verify reliability properties of such uniformly
parameterised cooperations, we use finite state semi-algorithms that
are independent of the concrete parameter setting.
|
BibTeX:
@incollection{ochsenschlaeger:rieke:2012b,
author = {Peter Ochsenschläger and Roland Rieke},
title = {{Reliability Aspects of Uniformly Parameterised Cooperations}},
booktitle = {ICONS 2012, The Seventh International Conference on Systems, February 29 - March 5, 2012 - Saint Gilles, Reunion Island},
pages = {25-34},
url = {http://www.thinkmind.org/download.php?articleid=icons_2012_2_10_20024},
publisher={IARIA},
isbn={978-1-61208-184-7},
year = {2012}
}
|
Peter Ochsenschläger and Roland Rieke (2012),
Security Requirements for Uniformly Parameterised Cooperations,
The 20th Euromicro International Conference on Parallel, Distributed and Network-Based Computing (PDP 2012)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract:
The specification of security requirements is an important step when specifying new systems and systems of systems or analysing existing systems with regard to security issues. A common way to formally specify security requirements is by means of safety and liveness properties.
The systems in the focus of this paper are uniformly parameterised cooperations. Such systems are characterised by the composition of a set of identical components. These components interact in a uniform manner described by the schedules of the partners. Such a kind of interaction is typical for scalable complex systems with a cloud or grid structure.
As a main result, a formalism to specify uniformly parameterised behaviour properties of cooperations is given. To capture possibilistic aspects of especially liveness properties, a modified satisfaction relation is used. For safety properties, this relation, which is called approximate satisfaction, is equivalent to the usual one.
|
BibTeX:
@inproceedings{ochsenschlaeger:rieke:2012a,
author = {Peter Ochsenschläger and Roland Rieke},
title = {Security Requirements for Uniformly Parameterised Cooperations},
booktitle = {Parallel, Distributed and Network-Based Processing (PDP), 2012 20th Euromicro International Conference on},
volume = {0},
issn = {1066-6192},
year = {2012},
pages = {288-292},
url = {http://doi.ieeecomputersociety.org/10.1109/PDP.2012.27},
publisher = {IEEE Computer Society},
address = {Los Alamitos, CA, USA},
}
|
Jörn Eichler and Roland Rieke (2011),
Model-based Situational Security Analysis,
6th International Workshop on Models@run.time in conjunction with MODELS 2011.
[Abstract]
[BibTeX]
[Paper (free access)]
[Author's version]
|
| Abstract: Security analysis is growing in complexity with the increase in functionality, connectivity, and dynamics of current electronic business processes. To tackle this complexity, the application of models in pre-operational phases is becoming standard practice. But also runtime models are increasingly applied to analyze and validate the actual security status of business process instances. In this paper we present an approach to support not only model-based evaluation of the current security status of business process instances but also to allow for decision support by analyzing close-future process states. Our approach is based on operational formal models derived from development-time process and security models. This paper exemplifies our approach utilizing real world processes from the logistics domain and demonstrates the systematic development and application of runtime models for situational security analysis.
|
BibTeX:
@incollection{eichler:rieke:2011,
author = {J\"orn Eichler and Roland Rieke},
title = {{Model-based Situational Security Analysis}},
booktitle = {Proceedings of the 6th International Workshop on Models@run.time at the ACM/IEEE 14th International Conference on Model Driven Engineering Languages and Systems (MODELS 2011), Wellington, New Zealand},
pages = {25-36},
volume = 794,
editors = {Nelly Bencomo, Gordon Blair, Betty Cheng, Robert France, Cédric Jeanneret},
publisher = {Nelly Bencomo, Gordon Blair, Betty Cheng, Robert France, Cédric Jeanneret},
series = {CEUR Workshop Proceedings},
url = {http://ceur-ws.org/Vol-794/paper_1.pdf},
issn={1613-0073},
year = {2011}
}
|
Peter Ochsenschläger and Roland Rieke (2011),
Security Properties of Self-similar Uniformly Parameterised Systems of Cooperations,
The 19th Euromicro Conference on Parallel, Distributed and Network-Based Computing (PDP 2011)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract: Uniform parameterisations of cooperations are defined in terms of
formal language theory, such that each pair of partners cooperates in
the same manner, and that the mechanism (schedule) to determine how
one partner may be involved in several cooperations, is the same for
each partner. Generalising each pair of partners cooperating in the
same manner, for such systems of cooperations a kind of
self-similarity is formalised. From an abstracting point of view,
where only actions of some selected partners are considered, the
complex system of all partners behaves like the smaller subsystem of
the selected partners. For verification purposes, so called
uniformly parameterised safety properties are defined. Such
properties can be used to express privacy policies as well as
security and dependability requirements. It is shown, how the
parameterised problem of verifying such a property is reduced by
self-similarity to a finite state problem. |
BibTeX:
@inproceedings{ochsenschlaeger:rieke:2011,
author = {Peter Ochsenschläger and Roland Rieke},
title = {{Security Properties of Self-similar Uniformly Parameterised Systems of Cooperations}},
booktitle = {Proceedings of the 19th Euromicro Conference on Parallel, Distributed and Network-Based Processing},
pages = {640-645},
doi = {http://doi.ieeecomputersociety.org/10.1109/PDP.2011.57},
publisher = {IEEE Computer Society},
address = {Los Alamitos, CA, USA},
year = {2011}
}
|
Kuntze, N., Rieke, R., Diederich, G., Sethmann, R., Sohr, K., Mustafa, T., and Detken, K.-O. (2010),
Secure mobile business information processing,
In Proceedings of 6th IEEE/IFIP International Symposium on Trusted Computing and Communications.
[Abstract]
[BibTeX]
[Paper]
[Vogue project version]
|
| Abstract: An ever increasing amount of functionality is incorporated into mobile phones--this trend will continue as new mobile phone platforms are more widely used such as the iPhone or Android. Along with this trend, however, new risks arise, especially for enterprises using mobile phones for security-critical applications such as business intelligence (BI). Although platforms like Android have implemented sophisticated security mechanisms, security holes have been reported [9]. In
addition, different stakeholders have access to mobile phones such as different enterprises, service providers, operators, or manufacturers. In order to protect security-critical business applications, a trustworthy mobile phone platform is needed. Starting with typical attack scenarios, we describe a security architecture for Android mobile phones based on the concepts of Trusted Computing. In particular, this architecture allows for a dynamic policy change to reflect the current environment the phone is being used in.
|
BibTeX:
@inproceedings{Kuntzea,
author = "Kuntze, Nicolai and Rieke, Roland and Diederich, G{\"u}nther and Sethmann, Richard and Sohr, Karsten and Mustafa, Tanveer and Detken, Kai-Oliver",
booktitle={Embedded and Ubiquitous Computing (EUC), 2010 IEEE/IFIP 8th International Conference on},
title={Secure Mobile Business Information Processing},
year={2010},
month={dec},
publisher = "IEEE/IFIP",
address = "Hongkong, China",
booktitle = {6th IEEE/IFIP International Symposium on Trusted Computing and Communications},
pages={672 -678},
doi={10.1109/EUC.2010.107}
}
|
Andreas Fuchs and Roland Rieke (2010),
Identification of Security Requirements in Systems of Systems by Functional Security Analysis,
In Architecting Dependable Systems VII, (Springer LNCS 6420)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract: Cooperating systems typically base decisions on information from their own components as well as on input from other systems. Safety critical decisions based on cooperative reasoning however raise severe concerns to security issues. Here, we address the security requirements elicitation step in the security engineering process for such systems of systems. The method comprises the tracing down of functional dependencies over system component boundaries right onto the origin of information as a functional flow graph. Based on this graph, we systematically deduce comprehensive sets of formally defined authenticity requirements for the given security and dependability objectives. The proposed method thereby avoids premature assumptions on the security architecture's structure as well as the means by which it is realised. Furthermore, a tool-assisted approach that follows the presented methodology is described. |
BibTeX:
@incollection{fuchs:rieke:2010,
author = {Andreas Fuchs and Roland Rieke},
title = {{Identification of Security Requirements in Systems of Systems by Functional Security Analysis}},
booktitle = {Architecting Dependable Systems VII},
editor = {Antonio Casimiro and Rogério de Lemos and Cristina Gacek},
publisher = {Springer},
series = {Lecture Notes in Computer Science},
volume = {6420},
year = {2010},
pages = {74--96},
doi={10.1007/978-3-642-17245-8_4},
url={http://dx.doi.org/10.1007/978-3-642-17245-8_4},
isbn = {978-3-642-17244-1}
}
|
Roland Rieke and Zaharina Stoynova (2010),
Predictive Security Analysis for Event-Driven Processes,
MMM-ACNS-2010, (Springer LNCS 6258)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract: This paper presents an approach for predictive security analysis in a business process execution environment. It is based on operational formal models and leverages process and threat analysis and simulation techniques in order to be able to dynamically relate events from different processes and architectural layers and evaluate them with respect to security requirements. Based on this, we present a blueprint of an architecture which can provide decision support by performing dynamic simulation and analysis while considering real-time process changes. It allows for the identification of close-future security-threatening process states and will output a predictive alert for the corresponding violation. |
BibTeX:
@incollection{Rieke:Stoynova:2010,
author = {Rieke, Roland and Stoynova, Zaharina},
affiliation = {Fraunhofer Institute for Secure Information Technology SIT, Darmstadt, Germany},
title = {Predictive Security Analysis for Event-Driven Processes},
booktitle = {Computer Network Security},
series = {Lecture Notes in Computer Science},
editor = {Kotenko, Igor and Skormin, Victor},
publisher = {Springer Berlin / Heidelberg},
isbn = {978-3-642-14705-0},
keyword = {Computer Science},
pages = {321-328},
volume = {6258},
url = {http://dx.doi.org/10.1007/978-3-642-14706-7_25},
doi = {10.1007/978-3-642-14706-7_25},
year = {2010}
}
|
Andreas Fuchs and Roland Rieke (2009),
Identification of authenticity requirements in systems of systems by functional security analysis,
In Workshop on Architecting Dependable Systems (WADS 2009), in Proceedings of the 2009 IEEE/IFIP Conference on Dependable Systems and Networks, Supplemental Volume.
[Abstract]
[BibTeX]
[Author's version]
|
| Abstract: Cooperating systems typically base decisions on information from their own components as well as on input from other systems. Safety critical decisions based on cooperative reasoning, such as automatic emergency braking of a vehicle, raise severe concerns to security issues. In this paper we address the security engineering process for such systems of systems. The presented authenticity requirements elicitation method is based on functional dependency analysis. It comprises the tracing down of functional dependencies over system boundaries right onto the origin of information. A dependency graph with a safety critical function as root and the origins of decision relevant information as leaves is used to deduce a set of authenticity requirements. This set is comprehensive and defines the maximal set of authenticity requirements from the given functional dependencies. Furthermore, the proposed method avoids premature assumptions on the architectural structure and mechanisms to implement security measures. |
BibTeX:
@inproceedings{fuchs:rieke:2009,
author = {Andreas Fuchs and Roland Rieke},
title = {Identification of authenticity requirements in systems of systems by functional security analysis},
booktitle = {Workshop on Architecting Dependable Systems (WADS 2009), in Proceedings of the 2009 IEEE/IFIP Conference on Dependable Systems and Networks, Supplemental Volume},
year = {2009},
pages={E29-E34},
}
|
Roland Rieke (2008),
Abstraction-based analysis of known and unknown vulnerabilities of critical information infrastructures,
International Journal of System of Systems Engineering (IJSSE). Vol. 1, pp. 59-77. InderScience.
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract: The systematic protection of critical information infrastructures requires an analytical process to identify the critical components and their interplay, to determine the threats and vulnerabilities, to assess the risks and to prioritise countermeasures where risk is unacceptable. The abstraction-based approach presented here builds on a model-based construction of an attack graph with constraints given by the network security policy. A unique feature of the presented approach is, that abstract representations of these graphs can be computed that allow comparison of focussed views on the behaviour of the system. In order to analyse resilience of critical information infrastructures against exploits of unknown vulnerabilities, generic vulnerabilities for each installed product and affected service are added to the model. The reachability analysis now considers every possible choice of product, and so all alternatives are evaluated in the attack graph. The impact of changes to security policies or network structure can be visualised by differences in the attack graphs. Results of this analysis support the process of dependable configuration of critical information infrastructures. |
BibTeX:
@article{Rieke08,
author = {Roland Rieke},
title = {Abstraction-based analysis of known and unknown vulnerabilities of critical information infrastructures},
journal = {International Journal of System of Systems Engineering (IJSSE)},
publisher = {Inderscience},
year = {2008},
volume = {1},
number={1/2},
pages = {59-77},
issn = {1748-0671},
doi={10.1504/IJSSE.2008.018131},
url ={http://dx.doi.org/10.1504/IJSSE.2008.018131}
}
|
Peter Ochsenschläger, Roland Rieke, and Zaharina Velikova (2008),
Die elektronische Krankenakte - Eine Sicherheitsstrategie,
In DACH Security 2008 - Bestandsaufnahme, Konzepte, Anwendungen, Perspektiven.
[Abstract]
[BibTeX]
[Proceedings]
[Author's version]
|
| Abstract: Diese Arbeit stellt ein Organisationsstruktur-basiertes Berechtigungskonzept am Beispiel der elektronischen Krankenakte vor. Ein ausführbares Modell der Sicherheitsstrategie erlaubt die vollständige Analyse des Systemverhaltens. Durch eigenschaftserhaltende Abstraktionen wird daraus eine kompakte Visualisierung von spezifischen Aspekten dieses Verhaltens möglich. Wegen der Kompaktheit der Darstellung lassen sich daraus die gewünschten Systemeigenschaften unmittelbar ablesen. Da die gewählten Abstraktionen eigenschaftserhaltend sind, folgen daraus nicht nur die erforderlichen Sicherheitseigenschaften sondern auch die Funktionssicherheit eines solchen Berechtigungskonzeptes trotz der gebotenen Datensparsamkeit. |
BibTeX:
@inproceedings{ORV08,
author = {P. Ochsenschläger and R. Rieke and Z. Velikova},
title = {Die elektronische Krankenakte - Eine Sicherheitsstrategie},
booktitle = {DACH Security 2008 - Bestandsaufnahme, Konzepte, Anwendungen, Perspektiven.},
year = {2008},
month = {June},
pages = {90-100},
isbn={978-3-00-024632-6}
}
|
Peter Ochsenschläger and Roland Rieke (2007),
Abstraction Based Verification of a Parameterised Policy Controlled System,
MMM-ACNS-07, (Springer CCIS 1)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract: Safety critical and business critical systems are usually controlled by policies with the objective to guarantee a variety of safety, liveness and security properties. Traditional model checking techniques allow a verification of the required behaviour only for systems with very few components. To be able to verify entire families of systems, independent of the exact number of replicated components, we developed an abstraction based approach to extend our current tool supported verification techniques to such families of systems that are usually parameterised by a number of replicated identical components. We demonstrate our technique by an exemplary verification of security and liveness properties of a simple parameterised collaboration scenario. Verification results for configurations with fixed numbers of components are used to choose an appropriate property preserving abstraction that provides the basis for an inductive proof that generalises the results for a family of systems with arbitrary settings of parameters. |
BibTeX:
@incollection{OR07,
author={Ochsenschl\"ager, Peter and Rieke, Roland},
title={Abstraction Based Verification of a Parameterised Policy Controlled System},
year={2007},
isbn={978-3-540-73985-2},
booktitle={Computer Network Security, Fourth International Conference on Mathematical Methods, Models, and Architectures for Computer Network Security, MMM-ACNS 2007 St. Petersburg, Russia, September 13-15, 2007 Proceedings},
volume={1},
series={Communications in Computer and Information Science},
editor={Gorodetsky, Vladimir and Kotenko, Igor and Skormin, VictorA.},
doi={10.1007/978-3-540-73986-9_19},
url={http://dx.doi.org/10.1007/978-3-540-73986-9_19},
publisher={Springer Berlin Heidelberg},
keywords={Formal analysis of security and liveness properties; security modelling and simulation; security policies; parameterised models},
pages={228-241},
language={English}
}
|
Apel, C., Jürgen Repp, Rieke, R., and Steingruber, J. (2007),
Modellbasiertes Testen der deutschen Gesundheitskarten,
In DACH Security 2007 - Bestandsaufnahme, Konzepte, Anwendungen, Perspektiven.
[Abstract]
[BibTeX]
[Proceedings]
[Author's version]
|
| Abstract: Dieser Beitrag beschreibt die Anwendung eines modellbasierten Verfahrens zur Testfolgengenerierung auf die deutschen elektronischen Gesundheitskarten, Heilberufsausweise und Sicherheitsmodulkarten, um deren Datensicherheit, Interoperabilität und Robustheit zu testen. Zur Modellierung der Chipkartenanwendungen werden asynchrone Produktautomaten (APA) verwendet. Daraus werden abstrakte Kommandofolgen für die Chipkarten berechnet, die dann in einem weiteren Schritt in konkrete ausführbare Kommandos übersetzt werden. Das verwendete Verfahren hat den Vorteil, dass damit komplexe Chipkartenanwendungen in kompakter und übersichtlicher Weise modelliert und automatisiert Testfolgen mit hoher Testabdeckung erzeugt werden können. |
BibTeX:
@inproceedings{ARRS07,
author = {C. Apel and J. Repp and R. Rieke and J. Steingruber},
title = {Modellbasiertes Testen der deutschen Gesundheitskarten},
booktitle = {DACH Security 2007 - Bestandsaufnahme, Konzepte, Anwendungen, Perspektiven.},
year = {2007},
month = {June},
pages = {338-346},
isbn={978-3-00-021600-8}
}
|
Peters, J., Rieke, R., Rochaeli, T., Steinemann, B., and Wolf, R. (2007),
A Holistic Approach to Security Policies - Policy Distribution with XACML over COPS,
In Proc. of the Second International Workshop on Views On Designing Complex Architectures (VODCA 2006). February 2007. Volume 168, Elsevier.
[Abstract]
[BibTeX]
[Paper (free access)]
|
| Abstract: The potentials of modern information technology can only be exploited, if the underlying infrastructure and the applied applications sufficiently take into account all aspects of IT security. This paper presents the platform architecture of the SicAri project, which aims to build a security platform for ubiquitous Internet usage, and gives an overview of the implicitly and explicitly used security mechanisms to enable access control for service oriented applications in distributed environments. The paper will introduce the security policy integration concept with a special focus on distribution of security policies within the service infrastructure for transparent policy enforcement. We describe in details our extensions of the COPS protocol to transport XACML payload for security policy distribution and policy decision requests/responses. |
BibTeX:
@inproceedings{Peters06,
author = {Jan Peters and Roland Rieke and Taufiq Rochaeli and Bj\"orn Steinemann and Ruben Wolf},
title = {{A Holistic Approach to Security Policies -- Policy Distribution with XACML over COPS}},
booktitle = {Proc. of the Second International Workshop on Views On Designing Complex Architectures (VODCA 2006)},
journal = {Electronic Notes in Theoretical Computer Science},
publisher = {Elsevier},
year = {2007},
month= {February},
volume = {168},
pages = {143-157},
issn = {1571-0661},
doi = {10.1016/j.entcs.2006.08.025},
url = {http://www.sciencedirect.com/science/article/pii/S1571066107000333},
}
|
Roland Rieke (2006),
Modelling and Analysing Network Security Policies in a Given Vulnerability Setting,
In Critical Information Infrastructures Security, First International Workshop (CRITIS 2006), (Springer LNCS 4347)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract: The systematic protection of critical information infrastructures requires an analytical process to identify the critical components and their interplay, to determine the threats and vulnerabilities, to assess the risks and to prioritise countermeasures where risk is unacceptable. This paper presents an integrated framework for model-based symbolic interpretation, simulation and analysis with a comprehensive approach focussing on the validation of network security policies. A graph of all possible attack paths is automatically computed from the model of an ICT network, of vulnerabilities, exploits and an attacker strategy. Constraints on this graph are given by a model of the network security policy. The impact of changes to security policies can be computed and visualised by finding differences in the attack graphs. A unique feature of the presented approach is, that abstract representations of these graphs can be computed that allow comparison of focussed views on the behaviour of the system. This guides optimal adaptation of the security policy to the given vulnerability setting. |
BibTeX:
@incollection{Rieke06,
author = {Roland Rieke},
title = {{Modelling and Analysing Network Security Policies in a Given Vulnerability Setting}},
booktitle = {Critical Information Infrastructures Security, First International Workshop, CRITIS 2006, Samos Island, Greece. Revised Papers},
editor={Javier Lopez},
year = {2006},
series = {Lecture Notes in Computer Science},
volume = {4347},
pages = {67-78},
isbn={978-3-540-69083-2},
doi={10.1007/11962977_6},
url={http://dx.doi.org/10.1007/11962977_6},
publisher={Springer Berlin Heidelberg},
keywords={threats analysis; attack simulation; critical infrastructure protection; network security policies; risk assessment; security modelling and simulation}
}
|
Roland Rieke (2004),
Tool based formal Modelling, Analysis and Visualisation of Enterprise Network Vulnerabilities utilising Attack Graph Exploration,
In U.E. Gattiker (Ed.), Eicar 2004 Conference CD-rom: Best Paper Proceedings.
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract:
A core concern of critical infrastructure protection is a careful analysis of what
parts of the information infrastructure really need protection and what are the
concrete threads as well as an evaluation of appropriate protection measures.
In this paper a methodology and a tool for the development and analysis of
operational formal models is presented that addresses these issues in the
context of network vulnerability analysis.
A graph of all possible attack paths is automatically computed from the model of
a government or enterprise network, of vulnerabilities, exploits and an attacker
strategy.
Based on this graph, security properties are specified and verified, abstractions
of the graph are computed to visualise and analyse compacted information
focussed on interesting aspects of the behaviour and cost-benefit analysis is
performed.
Survivability comes into play, when systems' countermeasures and the behaviour
of vital services it provides are also modelled and effects are analysed.
|
BibTeX:
@inproceedings{EICAR2004,
author = {Roland Rieke},
title = {Tool based formal Modelling, Analysis and Visualisation of Enterprise Network Vulnerabilities utilising Attack Graph Exploration},
booktitle = {In U.E. Gattiker (Ed.), Eicar 2004 Conference CD-rom: Best Paper Proceedings},
year = {2004},
month = {May},
location ={Copenhagen},
url = {http://publica.fraunhofer.de/dokumente/N-47447.html}
}
|
Michael Herfert, Andreas U. Schmidt, Peter Ochsenschläger, Jürgen Repp, Roland Rieke, Martin Schmucker, Steven Vettermann, Uwe Böttge, Cristina Escaleira, and Dirk Rüdiger (2004),
Implementierung von Security Policies in offenen Telekollaborationen,
In D-A-CH Security 2004. Sauerlach, Austria. Syssec.
[BibTeX]
[Paper]
|
BibTeX:
@inproceedings{AUS04A,
author = {Michael Herfert and Andreas U. Schmidt and Peter Ochsenschl\"{a}ger and J\"{u}rgen Repp and Roland Rieke and Martin Schmucker and Steven Vettermann and Uwe B\"{o}ttge and Cristina Escaleira and Dirk R\"{u}diger},
title = {{I}mplementierung von {S}ecurity {P}olicies in offenen {T}elekollaborationen},
year = {2004},
publisher = {syssec},
booktitle = {D.A.CH Security 2004},
address = {Sauerlach, Austria},
editor = {Patrick Horster},
pages = {37-39},
note = {ISBN 3-00-013137-X. }
url = {http://publica.fraunhofer.de/documents/N-22379.html}
}
|
Roland Rieke (2003),
Development of formal models for secure e-services,
In Eicar Conference 2003.
[BibTeX]
[Author's version]
|
BibTeX:
@inproceedings{EICAR2003,
author = {Roland Rieke},
title = {Development of formal models for secure e-services},
booktitle = {Eicar Conference 2003},
year = {2003},
month ={May},
}
|
Peter Ochsenschläger, Jürgen Repp, and Roland Rieke (2000),
Verification of Cooperating Systems - An Approach Based on Formal Languages,
In Proc. 13th International Florida Artificial Intelligence Research Society Conference (FLAIRS-2000), AAAI Press.
[BibTeX]
[Paper (free access)]
|
BibTeX:
@inproceedings{Ochsenschlaeger:Repp:Rieke:2000a,
author = {Peter Ochsenschl\"ager and J\"urgen Repp and Roland Rieke},
title = {Verification of Cooperating Systems -- An Approach Based on Formal Languages},
booktitle = {Proc. 13th International Florida Artificial Intelligence Research Society Conference (FLAIRS-2000)},
publisher = {AAAI Press},
location={Orlando, FL, USA},
year = {2000},
month= {May},
pages = {346-350},
note = {Copyright: 2000, American Association for Artificial Intelligence (www.aaai.org). All rights reserved.},
editors = {Etheredge, J. and Manaris, B.},
isbn = {0-1-57735-113-4},
url = {http://www.aaai.org/Papers/FLAIRS/2000/FLAIRS00-065.pdf}
}
|
Peter Ochsenschläger, Jürgen Repp, and Roland Rieke (2000),
The SH-Verification Tool,
In Proc. 13th International Florida Artificial Intelligence Research Society Conference (FLAIRS-2000), AAAI Press.
[BibTeX]
[Paper (free access)]
|
BibTeX:
@inproceedings{Ochsenschlaeger:Repp:Rieke:2000b,
author = {Peter Ochsenschl\"ager and J\"urgen Repp and Roland Rieke},
title = {The SH-Verification Tool},
booktitle = {Proc. 13th International Florida Artificial Intelligence Research Society Conference (FLAIRS-2000)},
publisher = {AAAI Press},
location={Orlando, FL, USA},
year = {2000},
month= {May},
pages = {18-22},
note = {Copyright: 2000, American Association for Artificial Intelligence (www.aaai.org). All rights reserved.},
url = {http://www.aaai.org/Papers/FLAIRS/2000/FLAIRS00-004.pdf}
}
|
Peter Ochsenschläger, Jürgen Repp, and Roland Rieke (2000),
Abstraction and composition - a verification method for co-operating systems,
Journal of Experimental and Theoretical Artificial Intelligence, Volume 12, Issue 4, 2000. Taylor and Francis.
[BibTeX]
[Paper (free access)]
[Author's version]
|
BibTeX:
@article{Ochsenschlaeger:Repp:Rieke:2000c,
author = {Peter Ochsenschl\"ager and J\"urgen Repp and Roland Rieke},
title = {Abstraction and composition -- a verification method for co-operating systems},
journal = {Journal of Experimental and Theoretical Artificial Intelligence},
year = {2000},
month={October},
volume = {12},
number={4},
pages = {447-459},
issn= {0952-813X},
doi ={10.1080/095281300454829},
url={http://dx.doi.org/10.1080/095281300454829},
publisher = {Taylor and Francis Ltd},
}
|
Peter Ochsenschläger, Jürgen Repp, Roland Rieke, and Ulrich Nitsche (1998),
The SH-Verification Tool - Abstraction-Based Verification of Co-operating Systems,
Formal Aspects of Computing, The International Journal of Formal Methods, Vol. 10.
[BibTeX]
[Paper]
[Author's version]
|
BibTeX:
@article{ORRN:98,
author = {Peter Ochsenschläger and J\"urgen Repp and Roland Rieke and Ulrich Nitsche},
title = {The SH-Verification Tool -- Abstraction-Based Verification of Co-operating Systems},
journal = {Formal Aspects of Computing, The International Journal of Formal Methods},
year = {1998},
volume = {10},
issue = {4},
pages = {381-404},
publisher={Springer-Verlag London Limited},
doi={10.1007/s001650050023},
issn={0934-5043},
url = {http://link.springer.com/article/10.1007\%2Fs001650050023}
}
|
Daniel Zelle, Roland Rieke, and Christoph Krauß (2019),
Security Test Platform for Autonomous Driving,
3. ACM COMPUTER SCIENCE IN CARS SYMPOSIUM (CSCS 2019)
[BibTeX]
[Extended abstract (free access)]
|
BibTeX:
@techreport{CSCS2019,
author = {Daniel Zelle and Roland Rieke and Christoph Krau\ss{}},
year = {2019},
month = {October},
title = {Security Test Platform for Autonomous Driving},
url = {https://cscs19.cispa.saarland/files/cscs19_camera_ready/19_TestbedSAD.pdf},
language = {english},
institution = {3. ACM COMPUTER SCIENCE IN CARS SYMPOSIUM (CSCS 2019)}
}
|
Roland Rieke (2019),
secUnity - Supporting the security community,
Abschlussbericht secUnity-Projekt (in German)
[BibTeX]
[Report (free access)]
|
BibTeX:
@techreport{other-secUnity,
author ={Roland Rieke},
year ={2019},
title = {{Abschlussbericht secUnity-Projekt}},
institution={Fraunhofer},
type={Schlussbericht},
number={F\"orderkennzeichen 16KIS0398},
month={June},
doi = {10.2314/KXP:1685931308},
publisher={Technische Informationsbibliothek u. Universit\"atsbibliothek},
url = {https://doi.org/10.2314/KXP:1685931308}
}
|
secUnity Supporting the security community (2019),
Cybersecurity Research: Challenges and Course of Action,
secUnity-Roadmap on Cybersecurity Research
[BibTeX]
[Paper (free access)]
|
BibTeX:
@techreport{secUnity2019,
author = {Michael Backes and Peter Buxmann and Claudia Eckert and
Thorsten Holz and J{\"{o}}rn M{\"{u}}ller-Quade and Oliver Raabe and
Michael Waidner and S{\'e}bastien Bardin and Herv{\'e} Debar and
Jochen Dinger and Sascha Fahl and Sebastian Faust and
Gloria Gonzalez Fuster and Stjepan Gro{\v{s}} and Joseph Hallett and
Magnus Harlander and Detlef Houdeau and Claude Kirchner and
Wolfgang Klasen and Volkmar Lotz and Evangelos Markatos and
Peter M{\"{o}}hring and Reinhard Posch and Steve Ritter and
Martin Schallbruch and Matthias Schunter and Melanie Volkamer and
Andreas Wespi and Adrian Engelbrecht and Andreas Fuchs and
Willi Geiselmann and Anna-Louise Grensing and Margareta Heidt and
Johann Heyszl and Matthias Hiller and Lukas J{\"{a}}ger and
Claudia Kawohl and Alexander Koch and Annika Kr{\"{a}}mer and
Ninja Marnau and Kathrin Noack and Roland Rieke and
Daniel Senf and Markus Springer and Anne Steinbr{\"{u}}ck and
Mario Strefler and Dennis Tatang},
editor = {M{\"{u}}ller-Quade, J{\"{o}}rn},
year = {2019},
title = {Cybersecurity Research: Challenges and Course of Action},
doi = {10.5445/IR/1000090060},
institution = {Karlsruher Institut f{\"{u}}r Technologie (KIT)},
keywords = {Cybersecurity, IT-Sicherheit},
pagetotal = {55},
url = {https://publikationen.bibliothek.kit.edu/1000090060},
language = {english}
}
|
Roland Rieke (2015),
ACCEPT - Anomaliemanagement in Computersystemen durch Complex Event Processing Technologie,
Schlussbericht ACCEPT-Projekt (in German)
[BibTeX]
[Report (free access)]
|
BibTeX:
@techreport{other-ACCEPT,
author ={Roland Rieke},
year ={2015},
title = {{ACCEPT - Anomaliemanagement in Computersystemen durch Complex Event Processing Technologie}},
institution={Fraunhofer},
type={Schlussbericht},
number={F\"orderkennzeichen 16BY1206A},
month={June},
doi = {10.2314/GBV:860456064},
publisher={Technische Informationsbibliothek u. Universit\"atsbibliothek},
url = {http://dx.doi.org/10.2314/GBV:860456064}
}
|
Peter Ochsenschläger and Roland Rieke (2015),
Pairs of Languages Closed under Shuffle Projection,
arXiv 1503.08602.
[Abstract]
[BibTeX]
[Paper (free access)]
[Author's version]
|
| Abstract:
Shuffle projection is motivated by the verification of safety properties of
special parameterized systems. Basic definitions and properties, especially
related to alphabetic homomorphisms, are presented. The relation between
iterated shuffle products and shuffle projections is shown. A special class of
multi-counter automata is introduced, to formulate shuffle projection in terms
of computations of these automata represented by transductions. This
reformulation of shuffle projection leads to construction principles for pairs
of languages closed under shuffle projection. Additionally, it is shown that
under certain conditions these transductions are rational, which implies
decidability of closure against shuffle projection. Decidability of these
conditions is proven for regular languages. Finally, without additional
conditions, decidability of the question, whether a pair of regular languages
is closed under shuffle projection, is shown. In an appendix the relation
between shuffle projection and the shuffle product of two languages is
discussed. Additionally, a kind of shuffle product for computations in
S-automata is defined.
|
BibTeX:
@techreport{ochsenschlaeger:rieke:2015,
author = {Peter Ochsenschl\"ager and Roland Rieke},
title = {{Pairs of Languages Closed under Shuffle Projection}},
url="http://arxiv.org/abs/1503.08602",
publisher={arXiv},
year = {2015}
}
|
Jürgen Repp and Roland Rieke (2013),
Predictive Security Analyser,
Deliverable D4.2.3,
FP7-257475 MASSIF European project
[BibTeX]
[Techreport]
|
BibTeX:
@techreport{other-D4.2.3,
title={{Predictive Security Analyser}},
author={J\"urgen Repp and Roland Rieke},
year={2013},
month={January},
type = {Deliverable},
number = {D4.2.3},
institution={FP7-257475 MASSIF European project},
url = {http://rieke.link/D4.2.3-Predictive_Security_Analyser_v1.0_final.pdf}
}
|
Carsten Rudolph and Roland Rieke (2012),
Como garantir a seguranca da informacao (Internet do Futuro),
In Brazilian RTI Magazine Oct. 2012
[BibTeX]
[Article]
|
BibTeX:
@article{rieke:rudolph:2012,
author = {Roland Rieke and Carsten Rudolph},
title = {Como garantir a seguranca da informacao (Internet do Futuro)},
journal = {Brazilian RTI Magazine},
year = {2012},
month={October},
pages = {70-73},
url = {http://www.arandanet.com.br/midiaonline/rti/2012/outubro/index.html},
address = {Sao Paulo Brazil}
}
|
Roland Rieke, Jürgen Repp, and Maria Zhdanova (2012),
Process Model and Dynamic Simulation and Analysis Modelling Framework,
Deliverable D4.2.2, FP7-257475 MASSIF European project
[BibTeX]
[Techreport]
|
BibTeX:
@techreport{other-D4.2.2,
title={{Process Model and Dynamic Simulation and Analysis Modelling Framework}},
author={Roland Rieke and J\"urgen Repp and Maria Zhdanova},
year={2012},
month={October},
type = {Deliverable},
number = {D4.2.2},
institution={FP7-257475 MASSIF European project},
url = {http://rieke.link/D4.2.2-Process_Model_and_Dynamic_Simulation_v1.0_final.pdf}
}
|
Maria Zhdanova, Jürgen Repp, and Roland Rieke (2012),
Multi-level Abstraction Concept,
Deliverable D4.1.2, FP7-257475 MASSIF European project
[BibTeX]
[Techreport]
|
BibTeX:
@techreport{other-D4.1.2,
title={{Multi-level Abstraction Concept}},
author={Maria Zhdanova and J\"urgen Repp and Roland Rieke},
year={2012},
month={October},
type = {Deliverable},
number = {D4.1.2},
institution={FP7-257475 MASSIF European project},
url = {http://rieke.link/D4.1.2-Multi-level_Abstraction_Concept_v1.0_final.pdf}
}
|
Andrew Hutchison and Roland Rieke (2012),
Measuring Progress in Cyber-Security: An Open Architecture for Security Measurement Consolidation,
2012 Workshop on Cyber Security and Global Affairs and Global Security Forum
[BibTeX]
[Short Paper]
|
BibTeX:
@conference{hutchison:rieke:2012,
author = {Andrew Hutchison and Roland Rieke},
title = {{Measuring Progress in Cyber-Security: An Open Architecture for Security Measurement Consolidation}},
booktitle = {2012 Workshop on Cyber Security and Global Affairs and Global Security Forum, Barcelona},
url = {http://rieke.link/CS-GA-2012-abstract-hutchison-rieke.pdf},
year = {2012},
month={June},
}
|
MASSIF Consortium (2012),
MASSIF white paper: Enhancing Security and Trustworthiness with Next-Generation Security Information and Event Management,
FP7-257475 MASSIF European project
[BibTeX]
[MASSIF White paper]
|
BibTeX:
@techreport{other-MASSIF-white,
author={MASSIF Consortium},
title={MASSIF white paper: Enhancing Security and Trustworthiness with Next-Generation Security Information and Event Management},
institution={FP7-257475 MASSIF European project},
organization={FP7-257475 MASSIF European project},
year={2012},
month={June},
url = {http://rieke.link/MASSIF_White_paper.pdf}
}
|
Paulo Verissimo, Nuno Neves, Alexander Goller, Alberto Roman Limancero, Susana González, Rubén Torres, Luigi Romano, Salvatore D'Antonio, Hervé Debar, Roland Rieke, Zaharina Stoynova, Igor Kotenko, Andrey Chechulin, Ricardo Jimenez-Peris, Claudio Soriente, Nizar Kheir, and Jouni Viinikka (2012),
MASSIF Architecture Document,
FP7-257475 MASSIF European project
[BibTeX]
[MASSIF Architecture document]
|
BibTeX:
@techreport{other-MASSIF-arch,
author={Paulo Verissimo and Nuno Neves and Alexander Goller and Alberto Roman
Limancero and Susana González and Rubén Torres and Luigi Romano and Salvatore D'Antonio and Hervé Debar and Roland Rieke and Zaharina Stoynova and Igor Kotenko and Andrey Chechulin and Ricardo Jimenez-Peris and Claudio
Soriente and Nizar Kheir and Jouni Viinikka},
title={MASSIF Architecture Document},
institution={FP7-257475 MASSIF European project},
organization={FP7-257475 MASSIF European project},
year={2012},
month={April},
url = {http://rieke.link/MASSIF_Architecture_document.pdf}
}
|
Hermann Kaindl, Marko Jäntti, Herwig Mannaert, Kazumi Nakamatsu, and Roland Rieke (2012),
Requirements Engineering for Software vs. Systems in General,
The Seventh International Conference on Systems (ICONS 2012)
[Abstract]
[BibTeX]
[Short Paper (free access)]
|
| Abstract:
Are there fundamental technical differences between requirements engineering for software vs. systems in general? It seems as though even functional requirements can mean something more general for a system including mechanical parts than for software alone. Quality requirements on safety deal with humans and their relationship with some real artifacts in their environment, so they cannot be dealt with by software alone. However, reliability of underlying software will be important in this context. While the internal structure of software will not normally be specified in its requirements, structure of a more general system may well be. These are just examples of what should be discussed. With regard to intelligent enterprises, there exist defined methodologies for enterprise modeling. Much as any other complex system, an enterprise may be better understood through modeling. Once an enterprise is better understood, it may be easier to make it intelligent. Whatever technical system is to be developed in an enterprise, it needs to fit into. By connecting enterprise modeling and requirements engineering, the likelihood of such a fit is increased. For software development, such connections have been worked out and are part of defined methodologies, some of them based on object-oriented modeling. Are they applicable to the development of general systems?
|
BibTeX:
@incollection{kjmnr:2012,
author = {Hermann Kaindl and Marko Jäntti and Herwig Mannaert and Kazumi Nakamatsu and Roland Rieke},
title = {{Requirements Engineering for Software vs. Systems in General}},
booktitle = {ICONS 2012, The Seventh International Conference on Systems, February 29 - March 5, 2012 - Saint Gilles, Reunion Island},
pages = {190-192},
url = {http://www.thinkmind.org/download.php?articleid=icons_2012_9_10_20020},
publisher={IARIA},
isbn={978-1-61208-184-7},
year = {2012},
month={February}
}
|
Jürgen Repp and Roland Rieke (2011),
Formal Specification of Security Properties,
Deliverable D4.2.1, FP7-257475 MASSIF European project
[BibTeX]
[Techreport]
|
BibTeX:
@techreport{other-D4.2.1,
title={{Formal Specification of Security Properties}},
author={J\"urgen Repp and Roland Rieke},
year={2011},
month={September},
type = {Deliverable},
number = {D4.2.1},
institution={FP7-257475 MASSIF European project},
url = {https://rieke.link/D4.2.1-Formal_Specification_of_Security_v1.0_final.pdf}
}
|
Andrew Hutchison and Roland Rieke (2011),
Management of Security Information and Events in Future Internet,
2011 Workshop on Cyber Security and Global Affairs
[BibTeX]
[Short Paper]
|
BibTeX:
@conference{hutchison:rieke:2011,
author = {Andrew Hutchison and Roland Rieke},
title = {{Management of Security Information and Events in Future Internet}},
booktitle = {2011 Workshop on Cyber Security and Global Affairs, Budapest},
url = {https://rieke.link/CS-GA-2011-hutchison-rieke-extended.pdf},
year = {2011},
month={June},
}
|
Roland Rieke (2011),
SIEM Systems of the Future,
2011 Effects+ Trustworthy ICT Research Roadmap Session
[BibTeX]
|
BibTeX:
@unpublished{talks-Effects+:2011,
author = {Roland Rieke},
title = {{SIEM} Systems of the Future},
note={Talk at the Effectsplus Trustworthy ICT Research Roadmap Session Cluster Meeting, Brussels},
month={March},
year={2011}
}
|
Peter Ochsenschläger and Roland Rieke (2010),
Behaviour Properties of Uniformly Parameterised Cooperations,
Technical Report SIT-TR-2010/2, 2010.
[Abstract]
[BibTeX]
[Paper]
|
| Abstract: In this paper we consider safety and liveness properties, where possibilistic aspects of especially liveness properties are captured by a modified satisfaction relation, called approximate satisfaction. The systems in the focus of this paper are uniformly parameterised cooperations. Such systems are characterised by the composition of a set of identical components. These components interact in a uniform manner described by the schedules of the partners. Such kind of interaction is typical for scalable complex systems with cloud or grid structure. As a main result, a finite state verification framework for uniformly parameterised behaviour properties is given. The keys to this framework are structuring cooperations into phases and defining periods of system behaviour. Finite state semi-algorithms that are independent of the concrete parameter setting are presented to verify behaviour properties of such uniformly parameterised cooperations. |
BibTeX:
@techreport{OR2010t2,
author = {Peter Ochsenschl\"ager and Roland Rieke},
title = {Behaviour Properties of Uniformly Parameterised Cooperations},
year = {2010},
number = {SIT-TR-2010/2},
url = {http://publica.fraunhofer.de/dokumente/N-212198.html}
}
|
Roland Rieke (2010),
Challenges for Systems of Systems Security Information and Event Management,
2010 Workshop on Cyber Security and Global Affairs
[BibTeX]
[Short Paper]
|
BibTeX:
@conference{talks-rieke:2010,
author = {Roland Rieke},
title = {{Challenges for Systems of Systems Security Information and Event Management}},
booktitle = {2010 Workshop on Cyber Security and Global Affairs,ETH,Zurich},
url = {http://rieke.link/CS-GA-2010-rieke-abstract.pdf},
year = {2010},
month={July},
}
|
Andreas Fuchs and Roland Rieke (2010),
Identification of Security Requirements for Vehicular Communication Systems,
2010 CAST-Workshop on Mobile Security for Intelligent Cars (EVITA project workshop)
[BibTeX]
[Short Paper]
[Techreport (free access)]
|
BibTeX:
@inproceedings{talks-CAST:2010,
editor = {Olaf Henniger},
booktitle = {Presentation slides from the EVITA project workshop},
author = {Andreas Fuchs and Roland Rieke},
title = {Identification of Security Requirements for Vehicular Communication Systems},
institution = {EVITA European project},
type = {Deliverable},
number = {D1.2.5.1},
year = {2010},
month= {July},
note = {CAST-Workshop on Mobile Security for Intelligent Cars, Darmstadt, Germany},
url = {https://evita-project.org/Publications/EVITAD1.2.5.1.pdf}
}
|
Roland Rieke (2010),
MASSIF: MAnagement of Security information and events in Service InFrastructures,
2010 Effective clustering in ICT Trust and Security
[BibTeX]
|
BibTeX:
@unpublished{talks-Effects+:2010,
author = {Roland Rieke},
title = {MAnagement of Security information and events
in Service InFrastructures},
note={Talk at the ICT 2010 Effectsplus networking session, Brussels},
month={September},
year={2010}
}
|
Peter Ochsenschläger and Roland Rieke (2010),
Uniform Parameterisation of Phase Based Cooperations,
Technical Report SIT-TR-2010/1, 2010.
[Abstract]
[BibTeX]
[Paper]
|
| Abstract: Uniform parameterisations of phase based cooperations are defined in terms of formal language theory. For such systems of cooperations a kind of self-similarity is formalised. Based on deterministic computations in shuffle automata a sufficient condition for self-similarity is given. Under certain regularity restrictions this condition can be verified by a semi-algorithm. For verification purposes, so called uniformly parameterised safety properties are defined, which e.g. can be used to express privacy policies. It is shown, how the parameterised problem of verifying such a property is reduced by self-similarity to a finite state problem. |
BibTeX:
@techreport{OR2010t,
author = {Peter Ochsenschl\"ager and Roland Rieke},
title = {Uniform Parameterisation of Phase Based Cooperations},
year = {2010},
number = {SIT-TR-2010/1},
url = {http://publica.fraunhofer.de/dokumente/N-212197.html}
}
|
Roland Rieke (2009),
Operational Models for Security and Dependability in Electronic Health Systems,
Dagstuhl-Workshop on Model-Based Design of Trustworthy Health Information Systems, No. 09073, Dagstuhl, Germany, 2009
[BibTeX]
[Abstracts Collection]
[Short Paper]
[Link to event]
|
BibTeX:
@inproceedings{rieke09a,
author = {Roland Rieke},
title = {Operational Models for Security and Dependability in Electronic Health Systems},
booktitle = {Model-Based Design of Trustworthy Health Information Systems},
publisher = {Schloss Dagstuhl - Leibniz-Zentrum fuer Informatik, Germany},
year = {2009},
number = {09073},
url = {http://drops.dagstuhl.de/opus/volltexte/2009/1998}
}
|
Alastair Ruddle, David Ward, Benjamin Weyl, Sabir Idrees,
Yves Roudier, Michael Friedewald, Timo Leimbach, Andreas
Fuchs, Sigrid Gürgens, Olaf Henniger, Roland Rieke,
Matthias Ritscher, Henrik Broberg, Ludovic Apvrille, Renaud
Pacalet, and Gabriel Pedroza (2009)
Security requirements for automotive on-board networks based on dark-side scenarios,
EVITA Deliverable D2.3
[Abstract]
[BibTeX]
[Techreport]
[Author's version]
|
| Abstract:
The objective of the EVITA project is to design, verify, and prototype an architecture for automotive on-board networks where security-relevant components are protected against tampering and sensitive data are protected against compromise. Thus, EVITA will provide a basis for the secure deployment of electronic safety aids based on vehicle-to-vehicle and vehicle-to-infrastructure communication. A key activity for the EVITA project is the capture of security requirements for the secure system architecture and associated software and hardware components based on a set of use cases and an investigation of security threat scenarios (dark-side scenarios). This document outlines the processes used to identify and evaluate security requirements, and details the results of their application to automotive on-board networks. It provides input to the secure on-board architecture design.
|
BibTeX:
@techreport{other-evita-d2.3,
author = {Alastair Ruddle and David Ward and Benjamin Weyl and Sabir Idrees
and Yves Roudier and Michael Friedewald and Timo Leimbach and Andreas
Fuchs and Sigrid G\"urgens and Olaf Henniger and Roland Rieke and
Matthias Ritscher and Henrik Broberg and Ludovic Apvrille and Renaud
Pacalet and Gabriel Pedroza},
title = {Security requirements for automotive on-board networks based on dark-side
scenarios},
institution = {EVITA project},
year = {2009},
type = {{EVITA Deliverable D2.3}},
url = {https://evita-project.org/deliverables.html}
}
|
Christophe Jouvray, Antonio Kung, Michel Sall,
Andreas Fuchs, Sigrid Gürgens, Roland Rieke
(2009)
Security and trust model,
EVITA Deliverable D3.1
[Abstract]
[BibTeX]
[Techreport]
[Author's version]
|
| Abstract:
The objective of the EVITA project is to design, verify, and prototype an architecture for
automotive on-board networks where security-relevant components are protected against
tampering and sensitive data are protected against compromise. Thus, EVITA will provide
a basis for the secure deployment of electronic safety aids based on vehicle-to-vehicle
and vehicle-to-infrastructure communication.
Designing a system respecting the criteria of security and trust is a complex task.
Security will cover various aspects such as dependability, integrity, authenticity, or even
privacy. It is thus possible to have confidence in a system where evidence is provided to
the user. To do this, taking into account security issues should begin early in the product
life cycle. Currently, model driven approaches are used in application design. Model
oriented approaches must be adjusted to take into account the security mechanisms.
This document analyzes different approaches to security architecture models and
specifies a suitable security and trust model for automotive on-board networks. Two main
solutions are proposed to adapt model approaches. The first one concerns directly the
model driven engineering by introducing all needed concepts into a model. The second
solution proposes a formal method for the refinement of security properties. High level
properties specified within a platform-independent model can be refined to properties
required by certain security mechanisms which in turn reflect the platform-specific
architecture chosen.
|
BibTeX:
@techreport{other-evita-d3.1,
author = {Christophe Jouvray and Antonio Kung and Michel Sall and Andreas
Fuchs and Sigrid G\"urgens and Roland Rieke},
title = {Security and trust model},
institution = {EVITA project},
year = {2009},
type = {{EVITA Deliverable D3.1}},
url = {http://evita-project.org/deliverables.html}
}
|
Roland Rieke and Peter Ebinger (2008),
Eine Sicherheitsarchitektur und deren Werkzeuge zur ubiquitären Internetnutzung,
SicAri Erfolgskontrollbericht (in German)
[BibTeX]
[Vorschau]
[Techreport]
|
BibTeX:
@techreport{other-SicAri,
author ={Roland Rieke and Peter Ebinger},
year ={2008},
title = {{Eine Sicherheitsarchitektur und deren
Werkzeuge zur ubiquit\"aren Internetnutzung : SicAri}},
institution={Fraunhofer},
type={Erfolgskontrollbericht},
number={F\"orderkennzeichen 01AK062B},
month={February},
publisher={Technische Informationsbibliothek u. Universit\"atsbibliothek},
url = {https://doi.org/10.2314/GBV:591262894}
}
|
Roland Rieke (2008),
Upcoming information security threats - an end-user perspective -,
2008 FORWARD workshop
[BibTeX]
[Short Paper]
|
BibTeX:
@unpublished{talks-FORWARD:2008,
author = {Roland Rieke},
title = {{Upcoming information security threats - an end-user perspective -}},
note = {Invited talk at 1st FORWARD Workshop, Goteborg, Sweden},
year = {2008},
month={April}
}
|
Roland Rieke (2007),
Wie ausführbare Modelle helfen, komplexe Systeme zu verstehen und sicherer zu steuern,
Vortragsreihe: Modelle für die Sicherheit und Zuverlässigkeit von Systemen, J.W.Goethe-Universität Frankfurt
[Abstract]
[BibTeX]
|
BibTeX:
@unpublished{talks-Frankfurt:2007,
author = {Roland Rieke},
title = {{Wie ausf\"uhrbare Modelle helfen, komplexe Systeme zu verstehen und sicherer zu steuern}},
note = {Vortragsreihe: Modelle f\"ur die Sicherheit und Zuverl\"assigkeit von Systemen, J.W.Goethe-Universit\"at Frankfurt},
year = {2007},
month={January}
}
|
Roland Rieke (2007),
Improving Resilience of Critical Information Infrastructures against Complex Threats,
2007 IFIP WG 10.4 Dependable Computing and Fault Tolerance workshop
[BibTeX]
|
BibTeX:
@unpublished{talks-IFIP:2007,
author = {Roland Rieke},
title = {{Improving Resilience of Critical Information Infrastructures against Complex Threats}},
note = {Invited talk at IFIP WG 10.4 Dependable Computing and Fault Tolerance, 51st Meeting, Guadeloupe, France},
year = {2007},
month={January}
}
|
Andreas Heinemann, Jan Oetting, Jan Peters, Roland Rieke, Taufiq Rochaeli, Markus Ruppert, Björn Steinemann, and Ruben Wolf (2006),
Enforcement of Security Policies within the SicAri-Platform,
SicAri - A security architecture and its tools for ubiquitous Internet usage, Deliverable PF5
[BibTeX]
[Techreport]
|
BibTeX:
@techreport{other-PF5,
author ={Andreas Heinemann and Jan Oetting and Jan Peters and Roland Rieke and Taufiq Rochaeli and Markus Ruppert and Bj\"orn Steinemann and Ruben Wolf},
year ={2006},
title = {{Enforcement of Security Policies within the SicAri-Platform}},
institution={SicAri Consortium},
number={PF5},
month={February},
url = {http://sicari.sourceforge.net/docs/SicAri-PF5.pdf}
}
|
Jan Peters, Roland Rieke, Taufiq Rochaeli, Björn Steinemann, and Ruben Wolf (2005),
Protocols for policy negotiation,
SicAri - A security architecture and its tools for ubiquitous Internet usage, Deliverable PE3
[BibTeX]
[Techreport]
|
BibTeX:
@techreport{other-PE3,
author = {Peters, J. and Rieke, R. and Rochaeli, T. and Steinemann, B. and Wolf, R.},
title = {{Protocols for policy negotiation}},
year = {2005},
institution={SicAri Consortium},
number = {PE3, Reportnr.: 05i018-FIGD},
url = {http://publica.fraunhofer.de/dokumente/N-45240.html}
}
|
Roland Rieke (2002),
Implementing the APA model for the symmetric Needham-Schroeder protocol in state transition pattern notation in the SH Verification Tool,
Technical Report
[BibTeX]
[Techreport]
|
BibTeX:
@techreport{other-NS-TR:2002,
author = {Roland Rieke},
title = {{Implementing the APA model for the symmetric Needham-Schroeder protocol in state transition pattern notation in the SH Verification Tool}},
year = {2002},
institution={Fraunhofer Institute for Secure Telecooperation SIT},
url = {http://rieke.link/NS-TR2002.pdf}
}
|
Peter Ochsenschläger, Jürgen Repp, and Roland Rieke (2002),
Simple Homomorphism Verification Tool - Tutorial,
Manual
[BibTeX]
[Paper]
|
BibTeX:
@manual{shvttutorial,
author = {Peter Ochsenschl\"ager and J\"urgen Repp and Roland Rieke},
title = {Simple Homomorphism Verification Tool -- Tutorial},
year = {2002},
url = {http://publica.fraunhofer.de/dokumente/N-47733.html}
}
|
Impressum Datenschutz
|

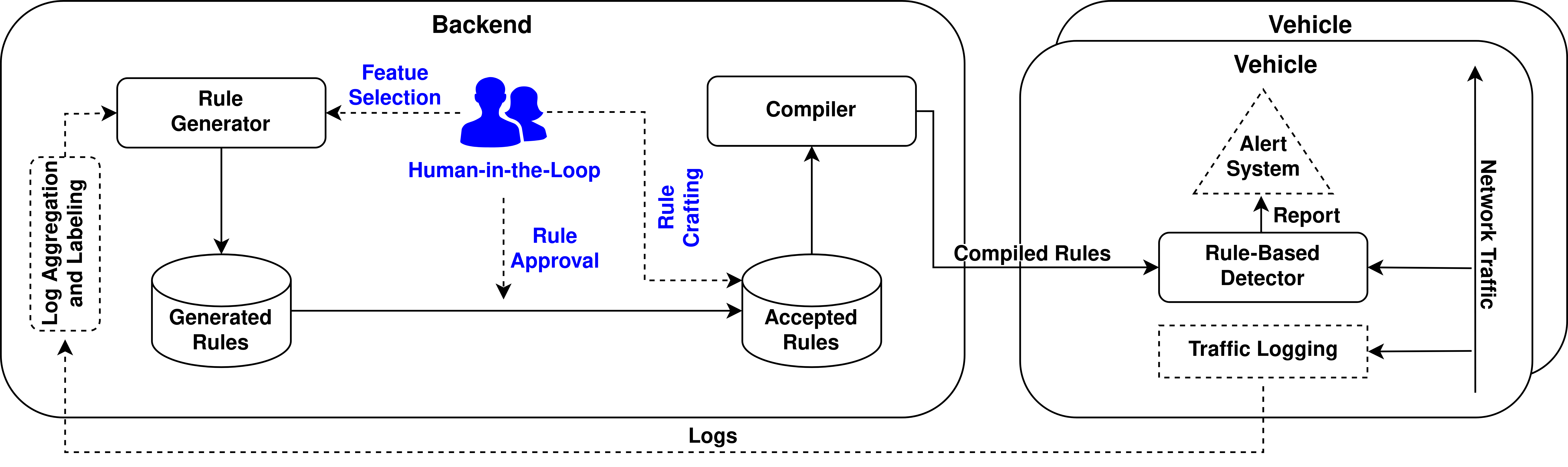
 Die Finalist*innen 2022
Die Finalist*innen 2022